Advanced Search
Content Type: Video
You can listen and subscribe to the podcast where ever you normally find your podcasts:
Spotify
Apple podcasts
Google podcasts
Castbox
Overcast
Pocket Casts
Peertube
Youtube
Stitcher
And more...
Content Type: News & Analysis
This week International Health Day was marked amidst a global pandemic which has impacted every region in the world. And it gives us a chance to reflect on how tech companies, governments, and international agencies are responding to Covid-19 through the use of data and tech.
All of them have been announcing measures to help contain or respond to the spread of the virus; but too many allow for unprecedented levels of data exploitation with unclear benefits, and raising so many red flags…
Content Type: Advocacy
Privacy International welcomes this opportunity to submit comments to the FATF consultation. The draft recommendation is an improvement on existing guidance that we have reviewed.
We also welcome the calls of the FATF for accommodations that will relieve burdens upon individuals who are being excluded from the financial sector, as a result of the FATF’s prior recommendations.
PI believes that identity systems must empower people. The initial question surrounding the development of any…
Content Type: News & Analysis
On 30 January 2020, Kenya’s High Court handed down its judgment on the validity of the implementation of the National Integrated Identity Management System (NIIMS), known as the Huduma Namba. Privacy International submitted an expert witness testimony in the case. We await the final text of the judgment, but the summaries presented by the judges in Court outline the key findings of the Court. Whilst there is much there that is disappointing, the Court found that the implementation of NIIMS…
Content Type: News & Analysis
Updated January 18th 2021
The Government of Myanmar is pushing ahead with plans to require anyone buying a mobile SIM card to be fingerprinted and hand over their ID cards, according to procurement documents circulated to prospective bidders.
The plans are a serious threat to privacy in a country lacking any data protection or surveillance laws and where minorities are systematically persecuted, and must be scrapped.
According to technical requirements developed by Myanmar’s Post and…
Content Type: News & Analysis
This creates a restraint on all people who merely seek to do as people everywhere do: to communicate freely.
This is a particularly worrying development as it builds an unreliable, pervasive, and unnecessary technology on top of an unnecessary and exclusionary SIM card registration policy. Forcing people to register to use communication technology eradicates the potential for anonymity of communications, enables pervasive tracking and communications surveillance.
Building facial recognition…
Content Type: Long Read
Photo by Nadine Shaabana on Unsplash
Digital identity providers
Around the world, we are seeing the growth of digital IDs, and companies looking to offer ways for people to prove their identity online and off. The UK is no exception; indeed, the trade body for the UK tech industry is calling for the development of a “digital identity ecosystem”, with private companies providing a key role. Having a role for private companies in this sector is not necessarily a problem: after all, …
Content Type: Long Read
Image credit: Emil Sjöblom [ShareAlike 2.0 Generic (CC BY-SA 2.0)]
Prepaid SIM card use and mandatory SIM card registration laws are especially widespread in countries in Africa: these two factors can allow for a more pervasive system of mass surveillance of people who can access prepaid SIM cards, as well as exclusion from important civic spaces, social networks, and education and health care for people who cannot.
Mandatory SIM card registration laws require that people provide personal…
Content Type: News & Analysis
This blogpost is a preview of the full 'Our Data Future' story, produced by Valentina Pavel, PI Mozilla-Ford Fellow, 2018-2019.
2030.
Four worlds.
One choice. Which one is yours?
All aboard! Time to step into the imaginarium. Explore four speculative future scenarios, examining how different ways of governing data create vastly different worlds. How is our digital environment going to look like in ten years' time? What’s going to be our relationship with data?
Each of us has a role in…
Content Type: Long Read
Whilst innovation in technology and data processing have provided individuals and communities with new opportunities to exercise their fundamental rights and freedoms, this has not come without risks, and these opportunities have not been enjoyed by all equally and freely.
Our relationships and interactions with governments and industry have become increasingly dependent on us providing more and more data and information about ourselves. And, it’s not only the information we provide knowingly…
Content Type: Examples
The State is not always the only actor involved in the surveillance of benefits claimants. Often those practices are encouraged, facilitated or conducted by private companies. South Africa for instance mandated MasterCard to help distribute benefits through biometric debit cards.
https://www.finextra.com/newsarticle/23941/south-africa-enlists-mastercard-to-distribute-welfare-through-biometric-debit-cards
Publication: FinExtra
Content Type: Examples
In Bangladesh, as part of the USAID and Bill and Melinda Gates Foundation supported programme “a2i” (Access to Information), the government has built a system to allow citizens to receive their welfare payment on a pre-paid debit card given to them at the Bangladesh Post Office after having been registered with their biometric data.
https://govinsider.asia/smart-gov/bangladesh-a2i-mobile-payments/
Author: Joshua Chambers and Nurfilzah Rohaidi
Publication: Gov Insider
Content Type: News & Analysis
The Committee on Foreign Investment in the United States (CFIUS) is trying to force the Chinese owner of the gay dating app Grindr to sell the app because of national security concerns. This is the first time the committee has considered the national security implications of a foreign social media app.
Early last year, the Chinese company Beijing Kunlun Tech purchased the Californian-based dating app. Kulun had already owned 60 per cent of Grindr since 2016. Yet, it is only now – with an…
Content Type: Press release
Key Points
A new report by Privacy International and the International Committee of the Red Cross finds that the humanitarian sector’s use of digital and mobile technologies could have detrimental effects for people receiving humanitarian aid.
This is because these digital systems generate a ‘data trail’ that is accessible and exploitable by third parties for non-humanitarian purposes. This metadata can be used to infer extremely intimate details, such as someone’s travel patterns or…
Content Type: Report
New technologies continue to present great risks and opportunities for humanitarian action. To ensure that their use does not result in any harm, humanitarian organisations must develop and implement appropriate data protection standards, including robust risk assessments.
However, this requires a good understanding of what these technologies are, what risks are associated with their use, and how we can try to avoid or mitigate them. This joint report by Privacy International and the…
Content Type: Examples
In January 2018 the Cyberspace Administration of China summoned representatives of Ant Financial Services Group, a subsidiary of Alibaba, to rebuke them for automatically enrolling its 520 million users in its credit-scoring system. The main complaint was that people using Ant's Alipay service were not properly notified that enrolling in the credit-scoring system would also grant Ant the right to share their personal financial data, including information about their income, savings, and…
Content Type: Examples
In 2015, a small number of Silicon Valley start-ups began experimenting with assessing prospective borrowers in developing countries such as Kenya by inspecting their smartphones. Doing so, they claimed, enabled them to charge less in interest than more traditional microlenders, since many of their target customers lack traditional credit ratings. The amount of data on phones - GPS coordinates, texts, emails, app data, and more obscure details such as how often the user recharges the battery,…
Content Type: Examples
Because banks often decline to give loans to those whose "thin" credit histories make it hard to assess the associated risk, in 2015 some financial technology startups began looking at the possibility of instead performing such assessments by using metadata collected by mobile phones or logged from internet activity. The algorithm under development by Brown University economist Daniel Björkegren for the credit-scoring company Enterpreneurial Finance Lab was built by examining the phone records…
Content Type: News & Analysis
Privacy International is celebrating Data Privacy Week, where we’ll be talking about privacy and issues related to control, data protection, surveillance and identity. Join the conversation on Twitter using #dataprivacyweek.
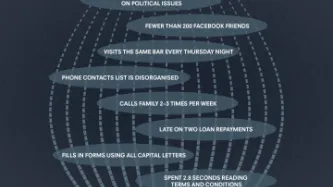
If you were looking for a loan, what kind of information would you be happy with the lender using to make the decision? You might expect data about your earnings, or whether you’ve repaid a loan before. But, in the changing financial sector, we are seeing more and more…
Content Type: Examples
Connecticut police have used the data collected by a murder victim's Fitbit to question her husband's alibi. Richard Dabate, accused of killing his wife in 2015, claimed a masked assailant came into the couple's home and used pressure points to subdue him before shooting his wife, Connie. However, her Fitbit's data acts as a "digital footprint", showing she continued to move around for more than an hour after the shooting took place. A 2015 report from the National Institute of…
Content Type: Report
Financial services are changing, with technology being a key driver. It is affecting the nature of financial services, from credit and lending through to insurance, and even the future of money itself.
The field of fintech is where the attention and investment is flowing. Within it, new sources of data are being used by existing institutions and new entrants. They are using new forms of data analysis.
These changes are significant to this sector and the lives of people it serves. This…
Content Type: News & Analysis
The Privacy International Network recently submitted joint stakeholder reports for seven partner countries - India, South Africa, Morocco, Tunisia, Brazil, the Philippines and Indonesia - as part of the 27th session of the Universal Periodic Review (1 to 12 May 2017).
Communications surveillance was a major area of concern, as we observed that these policies and practices remain largely opaque, complex and vague. In…
Content Type: News & Analysis
When it comes to tackling corruption, we need to critically engage with the role of technology. One technology in particular is biometrics, a technology that identifies and stores on a database the identity of an individual through some physical characteristic, usually fingerprints or an iris scan. Biometrics is increasingly being used in ID and voter registration schemes. It is a technology that raises privacy and data protection issues but notwithstanding…
Content Type: News & Analysis
This Sunday is International Women's Day. You could celebrate the considerable progress in legislating for women's equal rights. You could join a protest against political and legal inequality, discrepancies in women's access to healthcare, education and other social goods. You could thank your mom for delivering you.
Here at Privacy International, we want to commemorate the importance of this day by looking at some of the ways surveillance technologies can be used to control women and how the…
Content Type: News & Analysis
Humanitarian agencies are collecting personal information for Syrians caught in the crossfire of a drawn-out and bloody civil war. Indeed, refugees fleeing persecution and conflict, need to access services and protection offered by the world’s humanitarian community. But in the rush to provide necessary aid to those afflicted by the crisis in Syria, humanitarian organisations are overlooking a human right that also needs protecting: the right to privacy.
Humanitarian and aid agencies are…
Content Type: News & Analysis
Privacy International today is proud to announce our new project, Aiding Privacy, which aims to promote the right to privacy and data protection in the development and humanitarian fields. Below is an outline of the issues addressed in our new report released today, Aiding Surveillance.
New technologies hold great potential for the developing world. The problem, however, is that there has been a systematic failure to critically contemplate the potential ill effects of deploying technologies in…