Advanced Search
Content Type: Long Read
INTRODUCTION
In recent years, major tech platforms have been rapidly evolving their business models. Despite their dominance in various markets, tech giants like Google and Meta are venturing into new territories to expand their user base. One of the most striking ventures has been their foray into the "connectivity market" through substantial, and occasionally unsuccessful, investments in network infrastructure.
Many tech companies are investing resources into network infrastructure, either…
Content Type: Report
First published in 2017, PI’s Guide to International Law and Surveillance is an attempt to collate relevant excerpts from these judgments and reports into a single principled guide that will be regularly updated. This is the fourth edition of the Guide. It has been updated it to reflect the most relevant legal developments until March 2024.The Guide aspires to be a handy reference tool for anyone engaging in campaigning, advocacy, and scholarly research, on these issues. The fourth…
Content Type: Long Read
In June 2023, the UK government announced its proposal to expand its surveillance powers by, among others, forcing communications operators to undermine encryption or abstain from providing security software updates globally. Building on our response to the government’s plans, this piece explains why what they want to do puts every one of us at risk.
Why your trust (to technologies you use) matters
Surveillance and privacy are complex concepts to grasp – it’s part of the appeal to us at PI.…
Content Type: Advocacy
We are responding to the UK Government's consultation to expand its powers around Technical Capabilities Notices and National Security Notices.
Background
Following Edward Snowden's revelations about the illegal and expansive secret powers of the US and UK intelligence agencies, the UK Government took the opportunity to, rather than reflect on what powers are proportionate in the modern era, to expand its arsenal of surveillance powers.
One of the powers it added was the ability to issue…
Content Type: News & Analysis
We have been fighting for transparency and stronger regulation of the use of IMSI catchers by law enforcement in the UK since 2016. The UK police forces have been very secretive about the use of IMSI catchers – maintaining a strict “neither confirm nor deny” (NCND) policy. In our efforts to seek greater clarity we wrote to the UK body which monitors the use of covert investigatory powers, the Investigatory Powers Commissioner’s Office (IPCO), asking the Commissioner to revisit this…
Content Type: Report
End-to-end encryption (E2EE) contributes significantly to security and privacy. For that reason, PI has long been in favour of the deployment of robust E2EE.Encryption is a way of securing digital communications using mathematical algorithms that protect the content of a communication while in transmission or storage. It has become essential to our modern digital communications, from personal emails to bank transactions. End-to-end encryption is a form of encryption that is even more private.…
Content Type: Long Read
When you buy a brand-new low-cost phone, it’s likely to come pre-installed with insecure apps and an outdated operating system. What this means is that you or your loved ones could be left vulnerable to security risks or to having their data exploited. Privacy shouldn’t be a luxury. That’s why we advocate for companies to provide the latest security features and privacy protections for both low- and high-cost phones.
Content Type: News & Analysis
Today, the European Commission has concluded its Phase II in-depth review of the proposed acquisition of the health and fitness tracker Fitbit by Google, deciding that the merger can go through. While we welcome the commitments put forward by Google to mitigate some risks of compromising individuals' rights and competition, PI considers the effects of this merger will further strengthen Google's capacity to exploit our data.
On 15 June 2020, Google formally notified the European Commission of…
Content Type: Press release
The new satirical video is a critique of the government's reliance on 'technological solutionism' in the fight against Coronavirus and increasingly across public services more widely, and their willingness to then scapegoat ‘mutant algorithms’ when their hopes for technological panaceas inevitably fail.
The two-minute video splices together clips of Prime Minister Boris Johnson, cleverly editing his speeches so that he mouths sentences such as:
'Coronavirus won’t affect you if your immunity…
Content Type: News & Analysis
Samsung has announced that the company will commit to providing major software updates for three generations of the Android operating system, but only for its flagship models: the S10, S20, Note 10 and Note 20.
From our reading of the available information, this means that these models will be getting support, including the latest operating system, features and security updates, for three years (as new Android operating systems are released every year).
While this is welcome news, it only…
Content Type: Case Study
Privacy matters. It matters when you’re walking the streets of your home town and when you’re fleeing your home in search of safety. It matters if you’re at a protest or if you’re in bed.
Our wellbeing in each of these instances depends on the protection of our privacy. No situation can be fully understood in isolation.
Unjustifiable intrusions on our privacy become a weapon to eradicate communities and prey upon refugees and asylum seekers, push people away from protests in fear of…
Content Type: Case Study
Numerous sexist, mysoginistic, homophobic and racist practices are flourishing online, in ways that are harder for national authorities to stop than when abuse takes place offline. One of these practices is ‘revenge pornography’, which involves online distribution of private sexual images without the consent of the person depicted.
One victim of image based sexual abuse (more commonly known as revenge porn): Chrissy Chambers. Chrissy was 18 years old when her boyfriend convinced her to spend…
Content Type: Press release
MI6 has been forced to apologise to the Investigatory Powers Tribunal after two of its officers asked court staff to return documents relating to MI6’s use of agents and not show them to judges. The Tribunal suggested MI6’s actions were “inappropriate interference”.
The revelation emerged in an ongoing legal case considering what crimes intelligence informants are allowed to commit, after it was revealed that MI5 maintains a secret policy under which agents can be “authorised” to…
Content Type: News & Analysis
Name: Google/Fitbit merger
Age: Gestating
Appearance: A bit dodgy. One of the world’s biggest tech giants, trying to purchase a company that makes fitness tracking devices, and therefore has huge amounts of our health data.
I don’t get it. Basically Google is trying to buy Fitbit. As if Google doesn’t already have enough data about us, it now wants huge amounts of health data too.
Oh, Fitbit, that’s that weird little watch-type-thing that people get for Christmas, wear for about a month…
Content Type: Video
Immediately following the UK general election in December 2019, we worked with Open Rights Group to commission a YouGov poll about public understanding and public opinion about the use of data-driven campaigning in elections.
The poll used a representative sample of 1,664 adults across the UK population.
'Data-driven political campaigning' is about using specific data about you to target specific messages at you. So, for this might involve knowing that you are, for example, likely to…
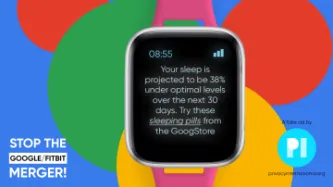
Content Type: Long Read
Monday, 16 June 2025
It’s 7:33 am. Lila’s GoogBit watch vibrates. “You got 6 hours and 57 minutes of sleep last night, including 2 hours and 12 minutes of deep sleep”, the watch reads. “In total, you tossed and turned for 15 minutes only”. Taking into account Lila’s online browsing activity, her sleep pattern, the recent disruptions in some of her other biorhythms, as well as her daily schedule, GoogBit watch has calculated the very best minute to wake her up.
Content Type: Press release
Today, the ICO has issued a long-awaited and critical report on Police practices regarding extraction of data from people's phones, including phones belonging to the victims of crime.
The report highlights numerous risks and failures by the police in terms of data protection and privacy rights. The report comes as a result of PI’s complaint, dating back to 2018, where we outlined our concerns about this intrusive practice, which involves extraction of data from devices of victims, witnesses…
Content Type: Press release
On 15 June 2020, Google formally notified the European Commission of its proposed acquisition of Fitbit, enabling them to capture a massive trove of sensitive health data that will expand and entrench its digital dominance. Privacy International is calling on EU regulators to block the merger.
In November 2019, Google announced its plan to acquire Fitbit, a company that produces and sells health tracking technologies and wearables - including smartwatches, health trackers and smart scales -…
Content Type: News & Analysis
This week, we read that a former Apple contractor who blew the whistle on the company’s programme to listen to users’ Siri recordings has decided to go public, in protest at the lack of action taken as a result of the July 2019 disclosures. The news adds to a series of revelations that have been reported over the past months.
While the issue raises serious questions regarding the compatibility of such practices with data protection laws, at the same time, it highlights a wider problem that…
Content Type: Case Study
You have the right to decent standards and dignity at work, and the right to join a union to protect yourself and your rights. That might come as a shock to Amazon - who have been using Covid-19 as a reason to undermine those rights.
Chris Smalls, an organiser and now former Amazon warehouse assistant manager, led a walkout at a New York City facility and within days he’d been fired under a dubious pretext.
The walkout was to ensure workers’ safety - they were asking for the warehouse to be…
Content Type: Long Read
Today is 1st May, an international day of protest. It also marks a year since PI launched our new programme of work called ‘Defending Democracy and Dissent’.
One year on we find ourselves in a situation where 1 May protests in the streets will not be going ahead. Rights have been restricted around the world. Sadly we’re seeing some actors exploit this public health crisis to enhance their own power, expanding surveillance and opportunism.
Against this challenging back-drop we wanted to…
Content Type: Explainer
In a scramble to track, and thereby stem the flow of new cases of Covid-19, Governments around the world are rushing to track the locations of their populace. One way to do this is to leverage the metadata held by mobile service providers (telecommunications companies - "Telcos" - such as Hutchison 3 (Also known as Three), Telefonica (Also known as O2), Vodafone, and Orange) in order to track the movements of a population, as seen in Italy, Germany and Austria, and with the European Commission…
Content Type: News & Analysis
A few weeks ago, its name would probably have been unknown to you. Amidst the covid-19 crisis and the lockdown it caused, Zoom has suddenly become the go-to tool for video chat and conference calling, whether it’s a business meeting, a drink with friends, or a much needed moment with your family. This intense rise in use has been financially good to the company, but it also came with a hefty toll on its image and serious scrutiny on its privacy and security practices.
While Zoom already had a…
Content Type: Case Study
Over the past decade targeted advertisement has become exponentially more invasive. To enable targeted advertisement, massive amounts of data about individuals are collected, shared and processed often without their knowledge or consent. This information about us is then used to profile us and micro-target us to sell us products or influence our views.
This is a significant intrusion to our privacy inevitably affects our perogative not to reveal our thoughts; not to have our thoughts…
Content Type: Long Read
On 15th April Margaret Atwood, author of the Handmaid's Tale, gave an interview to BBC Radio 5 Live where she commented that ‘people may be making arrangements that aren’t too pleasant, but it’s not a deliberate totalitarianism’. You can read more about the interview in the Guardian.
While we agree with Margaret Atwood that we are not necessarily entering an era of "deliberate totalitarianism" we have written the following open letter (download link at the bottom of the page) to her as a ‘…
Content Type: Case Study
Since August 2017 742,000 Rohingya people - including children - fled across the Myanmar border to Bangladesh, escaping what the UN labelled a “textbook example of ethnic cleansing”.
In this context of ethnoreligious violence, Facebook has been a central figure. For many in Myanmar “Facebook is the internet” - as of January 2018 around 19 million people in Myanmar were facebook users, this is roughly equal to the number of internet users in the country.
A New York Times report revealed that…
Content Type: News & Analysis
Amid calls from international organisations and civil society urging for measures to protect the migrant populations in Greece and elsewhere, last week, the European Commission submitted a draft proposal to amend the general budget 2020 in order to, among other measures, provide assistance to Greece in the context of the COVID-19 outbreak.
Both at the Turkish-Greek border and in the camps on the Greek islands, there are severe concerns not only about the dire situation in which these people…
Content Type: Examples
An engineering and computer science professor and his team from The Ohio State University discovered a design flaw in low-powered Bluetooth devices that leaves them susceptible to hacking.
Zhiqiang Lin, associate professor of computer science and engineering at the university, found the commonly used Bluetooth Low Energy devices, such as fitness trackers and smart speakers, are vulnerable when they communicate with their associated apps on the owner’s mobile phone.
"There is a fundamental…
Content Type: Examples
On November 3rd, 2019, [...] a critical vulnerability affecting the Android Bluetooth subsystem [was reported]. This vulnerability has been assigned CVE-2020-0022 and was now patched in the latest security patch from February 2020. The security impact is as follows:
On Android 8.0 to 9.0, a remote attacker within proximity can silently execute arbitrary code with the privileges of the Bluetooth daemon as long as Bluetooth is enabled. No user interaction is required and only the Bluetooth MAC…
Content Type: Examples
Researchers at the Center for IT-Security, Privacy and Accountability (CISPA) have identified a security vulnerability related to encryption on Bluetooth BR/EDR connections. The researchers identified that it is possible for an attacking device to interfere with the procedure used to set up encryption on a BR/EDR connection between two devices in such a way as to reduce the length of the encryption key used. In addition, since not all Bluetooth specifications mandate a minimum…