Advanced Search
Content Type: Long Read
18th December is International Migrants Day, a day to recognize both the contributions and continued struggles of migrants across the world.Migrants continue to face an increased level of human rights violations through hostile immigration policies and practices. At borders and beyond, their fundamental human rights and dignity are being violated through old and new technologies. These systems in place reinforce the dehumanising rhetoric of migrants, who are merely seeking asylum and a better…
Content Type: Advocacy
In the wake of Privacy International’s (PI) campaign against the unfettered use of Facial Recognition Technology in the UK, MPs gave inadequate responses to concerns raised by members of the public about the roll-out of this pernicious mass-surveillance technology in public spaces. Their responses also sidestep calls on them to take action.The UK is sleepwalking towards the end of privacy in public. The spread of insidious Facial Recognition Technology (FRT) in public spaces across the country…
Content Type: Long Read
1. What is the issue?Governments and international organisations are developing and accessing databases to pursue a range of vague and ever-expanding aims, from countering terrorism and investigating crimes to border management and migration control.These databases hold personal, including biometric, data of millions if not billions of people, and such data is processed by technologies, including Artificial Intelligence (AI), to surveil, profile, predict future behaviour, and ultimately make…
Content Type: Long Read
Social media is now undeniably a significant part of many of our lives, in the UK and around the world. We use it to connect with others and share information in public and private ways. Governments and companies have, of course, taken note and built fortunes or extended their power by exploiting the digital information we generate. But should the power to use the information we share online be unlimited, especially for governments who increasingly use that information to make material…
Content Type: Advocacy
At PI we have been observing with concern the rapid expansion of technologies in educational settings, which has included a wide array of tools that allow the surveillance of students and academic staff, to the detriment of their privacy and academic freedom. We consider this upcoming report as an essential platform to examine the intricate interplay between academic freedom, freedom of expression, and surveillance conducted by both public and private entities through Education…
Content Type: Advocacy
Privacy International's response to the call of submissions of the UN Special Rapporteur on the rights to freedom of peaceful assembly and of association on the tools and guidelines which may assist law enforcement in promoting and protecting human rights in the context of peaceful protests. The Special Rapporteur's report will be presented at the 55th session of the UN Human Rights Council.While PI recognises the role of law enforcement can play in facilitating the enjoyment of freedom of…
Content Type: Long Read
18th December is International Migrants Day. It’s a day designated by the United Nations, dedicated to recognising the “important contribution of migrants while highlighting the challenges they face.”On this day we wish to recognise in particular the countless human rights violations that people experience at borders and within hostile immigration systems. We thank those who survive these violations for sharing with us and others their experiences of such violations, and for accepting to…
Content Type: Explainer
The Free to Protest Guide Pakistan has been created by adapting Privacy International's (PI) Free to Protest Guide UK according to the laws and policies of Pakistan, in collaboration with PI and local activists in Pakistan.The Guide has been published in English, Urdu, Punjabi and Pashto.DISCLAIMER: This guide forms part of PI's global work to highlight the range of surveillance tools that law enforcement can use in the protest context, and how data protection laws can help guarantee…
Content Type: Advocacy
This was submitted by PI and EFF for the sixth session of the Ad Hoc Committee, which is due to consider the text in August 2023.
Our submission covers provisions in the chapters related to procedural measures and law enforcement, as well as international cooperation of the proposed UN Cybercrime treaty (full title: Comprehensive international convention on countering the use of information and communications technologies for criminal purposes). We also provide general comments on Article 54…
Content Type: Advocacy
Privacy International (PI) notes the Bureau’s text of the WHO convention, agreement or other international instrument on pandemic prevention, preparedness and response (“WHO CA+”).
PI has sought to closely follow and engage with the discussions leading up to the draft treaty, despite the significant limitations to civil society participation in the process. In February 2023, we intervened during the briefing organised by the INB bureau and published our comments on the zero draft of the WHO CA…
Content Type: Press release
Campaigners assembled outside Capita PLC’s Annual General Meeting in the City of London today (Thursday 11th May) are contesting the outsourcing company’s £114m contract to deliver 24/7 GPS monitoring services, used by the Home Office to surveil people without British citizenship.
Capita shareholders were greeted by a circling mobile billboard van and leaflets informing AGM attendees of the grave human rights and health risks associated with Capita’s GPS tracking contract. Charities Bail for…
Content Type: Advocacy
Privacy International welcomes the aim of the Cyber Resilience Act to bolster cybersecurity rules to ensure more secure hardware and software products. Nevertheless, we note that the proposal put forward by the European Commission contains certain shortcomings which could both hamper innovation and harm consumers who are increasingly relying on digital products and services.
It is essential these shortcomings, detailed below, are effectively addressed by the EU co-legislators through the…
Content Type: Advocacy
The submission provides PI’s information and analysis of some of the topics listed in the call. The widespread use of new technologies presents both opportunities and challenges for the protection of human rights, including the right to life and the right to privacy. PI believes that is essential that states take a human rights-centered approach in their use of these technologies, and ensure that their use is consistent with international human rights law. By doing so, states can ensure that…
Content Type: Report
PI has been fighting against police using intrusive & disproportionate surveillance technologies at protests around the world for years. Unregulated surveillance and indiscriminate intrusions on our privacy have a chilling effect on the right to freedom of assembly.
We've fought to uncover the types of technologies that police secretly deploy at protests, and we have detailed how protesters around the world can try to protect their intimate and sensitive data from being captured by the…
Content Type: Advocacy
Following our comments on the draft Treaty text, PI's intervention, during the fourth session, focused on the provisions of the draft Treaty that deal with procedural measures and law enforcement. Specifically, we emphasised that the investigative measures contained in the draft Treaty should only be limited to serious offences only that are established by the Treaty. In addition, we urged delegates to remove a provision contained in the draft Treaty text that would allow authorities to exploit…
Content Type: Report
Introduction
Several policy initiatives are in progress at the EU level. They seek to address the sustainability of connected devices such as smartphones, tablets and smart speakers. While initiatives to extend the useful life of hardware are important, software must not be ignored. Almost any digital device with which we interact today relies on software to function, which acts as a set of instructions that tells the hardware what to do. From smart thermostats to smart speakers, to our…
Content Type: Press release
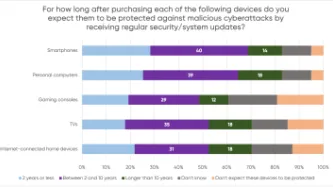
A YouGov survey commissioned by PI shows that consumers expect their smartphones, computers, smart TVs and gaming consoles to receive security updates for a much longer period than what several manufacturers actually provide, leaving consumers with expensive tech that is vulnerable to cyberattacks.
The majority of consumers in the survey assumed their devices would be protected beyond two years, but current industry practices fail to meet these expectations. PI investigated the software…
Content Type: Advocacy
On 30 March 2022, the European Commission published a proposal for a directive empowering consumers for the green transition, which is is designed to enhancing consumer rights in making informed choices in order to play an active role in the transition to a climate-neutral society. At the moment, the proposal is being discussed by the Committee on the Internal Market and Consumer Protection of the European Parliament.
PI welcomes the aim of the proposal to enhance consumer rights, particularly…
Content Type: Press release
The European Ombudswoman, Emily O’Reilly, has launched two new investigations into Frontex, the European Border and Coast Guard Agency, and into the European External Action Service (EEAS), the EU’s diplomatic agency, in relation to their support to non-EU countries to develop surveillance capabilities and, in particular, their lack of prior human rights risk and impact assessments.
The investigations, opened on 5 October 2022, come in response to complaints filed by Privacy International,…
Content Type: Advocacy
Now is the time to strengthen not weaken data protection to keep us all safe. Here we outline some edited areas of our consultation response that highlight the impact of the proposed loss or weakening of many important protections:
The proposal to broadening consent and further processing for research purposes:
PI urges caution with regard to provisions that seek to potentially undermine the strict conditions around obtaining consent. The GDPR placed stronger conditions on obtaining consent…
Content Type: Advocacy
In line with WHO's commitment to a human rights-based approach to health, Privacy International believes the following elements procedural and substantive elements must be included:
Open, inclusive and multi-stakeholder process
The drafting and negotiation process of this international instrument must allow for the meaningful participation of a wide range of civil society organisations (CSOs) and reflect the commitment from the WHO and Member States to receive and respond to CSOs…
Content Type: News & Analysis
In a ruling handed down on 14 October 2021 by the High Court of Kenya in relation to an application filed by Katiba Institute calling for a halt to the rollout of the Huduma card in the absence of a data impact assessment, the Kenyan High Court found that the Data Protection Act applied retrospectively.
Background to the case
Huduma Namba as initially proposed
In January 2019, the Kenyan Statute Law (Miscellaneous Amendment) Act No. 18 of 2018 came into effect, introducing a raft of amendments…
Content Type: Video
Please note the views expressed in the video are the interviewee's own and do not necessarily reflect the views of PI.
In his interview, Alexandru told us that he started to work for Uber in 2018. Despite being aware of negative experiences of others, he felt that everything was running smoothly, and for a while, Uber met his expectations.
However, in 2021, he received a notice from Uber that they had noticed fraudulent activity associated with his account. He went on social media and…
Content Type: Video
Please note the views expressed in the video are the interviewee's own and do not necessarily reflect the views of PI.
Driver X (he wishes to remain anonymous) has been working for Uber for five years. After working for Uber for two and half years, he suddenly received a message telling him that his account had been temporarily suspended and asking him not to call Uber while the investigation was pending. He was baffled, as he had an excellent record and rating, with plenty of positive…
Content Type: Long Read
What if your boss was an algorithm? What would you do if your employer suddenly fired you or reduced your pay without telling you why? And without being willing to give you a reason when you ask for one?
This is not science fiction or some far-fetched reality. Millions of people worldwide are working in the gig economy sector for companies like Uber, Deliveroo, Bolt, Just Eat… And this could be the future of work for people working outside the gig economy, as surveillance technologies are…
Content Type: Video
Update: Pa has since won a settlement from UberPlease note the views expressed in the video are interviewee's own and do not necessarily reflect the views of PI.Pa used to work for Uber. After some time, Uber started asking him to submit a picture of himself to the platform to confirm it was indeed him who had completed the job. However, with time, the frequency of the requests increased. In the beginning, the requests for a picture only happened once a week, but as time went by Pa told us that…
Content Type: Advocacy
Our environment is increasingly populated by devices connected to the Internet, from computers and mobile phones to sound systems and TVs to fridges, kettles, toys, or domestic alarms. There has been research into the negative safety and privacy impacts of inadequate security provided by the software in such devices (such as the creation of large scale botnets). This is also the case with outdated security, a risk enabled by software support periods that are shorter than a product’s usable life…
Content Type: Advocacy
On 6 August 2021, the World Health Organisation (WHO) published its technical specifications and implementation guidance for “Digital Documentation of COVID-19 Certificates: Vaccination Status” (DDCC:VS) following months of consultations. As governments around the world are deploying their own Covid-19 certificates, guidance from the global health agency was expected to set a global approach, and one that prioritises public health. As such, we would expect the WHO to identify what these…
Content Type: News & Analysis
Today Apple announced a set of measures aimed at improving child safety in the USA. While well-intentioned, their plans risk opening the door to mass surveillance around the world while arguably doing little to improve child safety.
Among the measures, Apple has announced that it is to introduce “on-device machine learning” which would analyse attachments for sexually explicit material, send a warning, and begin scanning every photo stored on its customers’ iCloud in order to detect child…
Content Type: News & Analysis
It is difficult to imagine a more intrusive invasion of privacy than the search of a personal or home computer ... when connected to the internet, computers serve as portals to an almost infinite amount of information that is shared between different users and is stored almost anywhere in the world.
R v Vu 2013 SCC 60, [2013] 3 SCR 657 at [40] and [41].
The controversial Police Crime Sentencing and Courts Bill includes provision for extracting data from electronic devices.
The Bill…