Advanced Search
Content Type: Advocacy
Privacy International responded to the call for submissions on Zimbabwe’s Cyber Security and Data Protection Bill, 2019.
According to its Memorandum, the Bill seeks to “consolidate cyber related offences and provide for data protection with due regard to the Declaration of Rights under the Constitution and the public and national interest.” The Bill also proposes the establishment of a Cyber Security Centre and a Data Protection Authority.
In its submission, PI applauds the positive aspects…
Content Type: Long Read
What Do We Know?
Palantir & the NHS
What You Don’t Know About Palantir in the UK
Steps We’re Taking
The Way Forward
This article was written by No Tech For Tyrants - an organisation that works on severing links between higher education, violent tech & hostile immigration environments.
Content Type: Case Study
The Ugandan government has a running contract with the Chinese tech giant, Huawei, to supply and install CCTV cameras along major highways within the capital, Kampala, and other cities.
While details of the contract remain concealed from the public, the Uganda Police Force (UPF) released a statement, simply confirming its existing business partnership for telecommunication and surveillance hardware, and software between the security force and Huawei. However, it is not clear whether the…
Content Type: News & Analysis
IMSI catchers (or stingrays as they are known in the US) are one of the surveillance technologies that has come to the forefront again in the protests against police brutality and systemic racism that have been sparked by the murder of George Floyd on 25 May 2020.
An International Mobile Subscriber Identity catcher – in short an “IMSI catcher” – is an intrusive piece of technology that can be used to locate and track all mobile phones that are switched on in a certain area. It does so by…
Content Type: Long Read
There are few places in the world where an individual is as vulnerable as at the border of a foreign country.
As migration continues to be high on the social and political agenda, Western countries are increasingly adopting an approach that criminalises people at the border. Asylum seekers are often targeted with intrusive surveillance technologies and afforded only limited rights (including in relation to data protection), often having the effect of being treated as “guilty until proven…
Content Type: Explainer
Hello friend,
You may have found your way here because you are thinking about, or have just submitted, a Data Subject Access Request, maybe to your Facebook advertisers like we did. Or maybe you are curious to see if Policing, Inc. has your personal data.
The right to access your personal data (or access right) is just one of a number of data rights that may be found in data protection law, including the European Union's General Data Protection Regulation, better known as "GDPR", which took…
Content Type: Long Read
Introduction
In August 2019, when Facebook announced a few new features for advertisers such as ads in search, PI decided to take an in-depth look at what features the company offers its users when it comes to understanding its advertising practices. One of these features, which caught our attention is Facebook Ads Preference, a tool that among other things, lists businesses/advertisers that have uploaded your personal data to target you with (or exclude you from) ads on the platform.
Content Type: News & Analysis
Yesterday, Amazon announced that they will be putting a one-year suspension on sales of its facial recognition software Rekognition to law enforcement. While Amazon’s move should be welcomed as a step towards sanctioning company opportunism at the expense of our fundamental freedoms, there is still a lot to be done.
The announcement speaks of just a one-year ban. What is Amazon exactly expecting to change within that one year? Is one year enough to make the technology to not discriminate…
Content Type: Advocacy
Last week, Privacy International joined more than 30 UK charities in a letter addressed to the British Prime Minister Boris Johnson, following his recent declaration, asking him to lift No Recourse to Public Funds (NRPF) restrictions.
Since 2012, a ‘NRPF condition’ has been imposed on all migrants granted the legal right to live and work in the UK. They are required to pay taxes, but they are not permitted to access the public safety net funded by those taxes.
This is not a topic we are known…
Content Type: Long Read
This article has been written by our partner organisation InternetLab. Read this article in Portuguese here.
Over the last months, the organisation InternetLab has researched privacy, data protection, gender, and social protection, focusing on the beneficiaries of the Bolsa Familia Program (PBF). The PBF is the most extensive Brazilian cash transfer program, and its functioning is linked to CadÚnico, a database that comprises 40% of the country’s population. Moreover, it is a program whose…
Content Type: Case Study
Since August 2017 742,000 Rohingya people - including children - fled across the Myanmar border to Bangladesh, escaping what the UN labelled a “textbook example of ethnic cleansing”.
In this context of ethnoreligious violence, Facebook has been a central figure. For many in Myanmar “Facebook is the internet” - as of January 2018 around 19 million people in Myanmar were facebook users, this is roughly equal to the number of internet users in the country.
A New York Times report revealed that…
Content Type: Case Study
There are 29.4 million refugees and asylum seekers across the globe today. These are people who have fled their countries due to conflict, violence or persecution seeking protection in safer environments.
People have protected those in need fleeing from dire situations since antiquity. However, over recent years, European countries have become increasingly hostile towards refugees - treating them as criminals instead of people in need.
In 2017, German authorities passed a…
Content Type: News & Analysis
This piece was originally published by Unwanted Witness here.
Today marks exactly one year since Uganda passed its data protection law, becoming the first East African country to recognize privacy as a fundamental human right, as enshrined in Art 27 of the 1995 Uganda Constitution as well as in regional and International laws.
The Data Protection and Privacy Act, 2019 aims to protect individuals and their personal data by regulating processing of personal information by state and non-state…
Content Type: Long Read
Background
Kenya’s National Integrated Identity Management Scheme (NIIMS) is a biometric database of the Kenyan population, that will eventually be used to give every person in the country a unique “Huduma Namba” for accessing services. This system has the aim of being the “single point of truth”, a biometric population register of every citizen and resident in the country, that then links to multiple databases across government and, potentially, the private sector.
NIIMS was introduced…
Content Type: Long Read
This piece was written by Aayush Rathi and Ambika Tandon, who are policy officers at the Centre for Internet and Society (CIS) in India. The piece was originally published on the website Economic Policy Weekly India here.
In order to bring out certain conceptual and procedural problems with health monitoring in the Indian context, this article posits health monitoring as surveillance and not merely as a “data problem.” Casting a critical feminist lens, the historicity of surveillance practices…
Content Type: Long Read
Valentine’s Day is traditionally a day to celebrate relationships, but many relationships that begin romantically can quickly become controlling, with partners reading emails, checking texts and locations of social media posts. This can be just the beginning.
Today, Friday 14th February, Privacy International and Women’s Aid are launching a series of digital social media cards giving women practical information on how to help stay safe digitally from control and abuse.
Did you know…
Content Type: News & Analysis
Privacy shouldn’t be a luxury.
Google claim to agree with us - we know that because Sundar Pichai, their CEO, said so this May in the New York Times. And yet, Google are enabling an ecosystem that exploits people who own low-cost phones.
Today we, along with over 50 organisations including Amnesty International, DuckDuckGo, and the ACLU are asking Google to step up, and we’re asking you to join us in pressuring them to do the right thing.
Sign the petition
Google has the power to…
Content Type: Advocacy
You can find the letter below. Add your voice to this campaign by signing our petition if you believe that its time Google stopped enabling exploitation.
Note: This letter is also available in French and Spanish
Dear Mr. Pichai,
We, the undersigned, agree with you: privacy cannot be a luxury offered only to those people who can afford it.
And yet, Android Partners - who use the Android trademark and branding - are manufacturing devices that contain pre-installed apps that cannot be deleted…
Content Type: Advocacy
Puede encontrar la carta a continuación. Agregue su voz a esta campaña firmando nuestra petición si cree que es hora de que Google deje de permitir la explotación.
Nota: Esta carta también está disponible en francés e inglés.
Estimado Sr. Pichai,
Nosotros, los firmantes, estamos de acuerdo con usted: la privacidad no puede ser un lujo reservado para las personas que tienen la capacidad de pagar por ella.
Sin embargo, los socios de Android Partner –que utilizan la marca y la imagen de…
Content Type: Advocacy
Vous pouvez trouver la lettre ci-dessous. Ajoutez votre voix à cette campagne en signant notre pétition si vous pensez qu'il est temps que Google cesse d'activer l'exploitation.
Ce contenu est également disponible en anglais et en espagnol.
Cher M. Pichai,
Nous, les organisations signataires, sommes d’accord avec vous :
la vie privée n’est pas un luxe, offert seulement à ceux qui en ont les moyens.
Pourtant, les « Android Partners » – qui utilisent la marque déposée…
Content Type: News & Analysis
On 24 October 2019, the Swedish government submitted a new draft proposal to give its law enforcement broad hacking powers. On 18 November 2019, the Legal Council (“Lagråd”), an advisory body assessing the constitutionality of laws, approved the draft proposal.
Privacy International believes that even where governments conduct hacking in connection with legitimate activities, such as gathering evidence in a criminal investigation, they may struggle to demonstrate that hacking as…
Content Type: Long Read
The pressing need to fix our cybersecurity (mis)understandings
Despite all the efforts made so far by different, cybersecurity remains a disputed concept. Some states are still approving cybersecurity laws as an excuse to increase their surveillance powers. Despite cybersecurity and cybercrime being different concepts, the confusion between them and the broad application of criminal statutes is still leading to the criminalise legitimate behaviour.
All of this represents a sizable challenge…
Content Type: News & Analysis
Today, the High Court of South Africa in Pretoria in a historic decision declared that bulk interception by the South African National Communications Centre is unlawful and invalid.
The judgment is a powerful rejection of years of secret and unchecked surveillance by South African authorities against millions of people - irrespective of whether they reside in South Africa.
The case was brought by two applicants, the amaBhungane Centre for Investigative Journalism and journalist Stephen…
Content Type: Advocacy
Privacy International's submission to the consultation initiated by the UN Special Rapporteur on counter-terrorism and human rights on the impact on human rights of the proliferation of “soft law” instruments and related standard-setting initiatives and processes in the counter-terrorism context.
In this submission Privacy International notes its concerns that some of this “soft law” instruments have negative implications on the right to privacy leading to violations of other human…
Content Type: Advocacy
In March 2019, Privacy International responded to a call for evidence for an inquiry by the UK Parliament's Joint Committee on Human Rights into "The Right to Privacy (Article 8) and the Digital Revolution".
Our suggestions included that, the human rights framework should support:
Increasing individuals’ control over their data to encourage the design of technologies that protect peoples’ autonomy and privacy.
Increasing security to result in more rights and protections for…
Content Type: Advocacy
The United Nations Special Rapporteur on extreme poverty and human rights, Philip Alston, is preparing a thematic report to the UN General Assembly on the human rights impacts, especially on those living in poverty, of the introduction of digital technologies in the implementation of national social protection systems. The report will be presented to the General Assembly in New York in October 2019.
As part of this process, the Special Rapporteur invited all interested governments, civil…
Content Type: Advocacy
Refugees are among the most vulnerable people in the world. From the moment they flee their homes, as they pass through 'temporary' places such as refugee camps and detention centres to their 'final' destinations, they are continuously exposed to threats. In the digital age, these threats are increasingly being driven by the processing of vast amounts of highly sensitive personal data: from enrollment and registration processes needed for them to access services, to their identification and…
Content Type: News & Analysis
Planning and participating in peaceful protests against governments or non-state actors’ policies and practices requires the capacity of individuals to communicate confidentially without unlawful interference. From protests in support of LGBTI rights to protests against specific projects that undermine local communities’ wellbeing, these movements would not have been possible without the ability to exchange ideas and develop plans in private spaces.
Unlawful interference with…
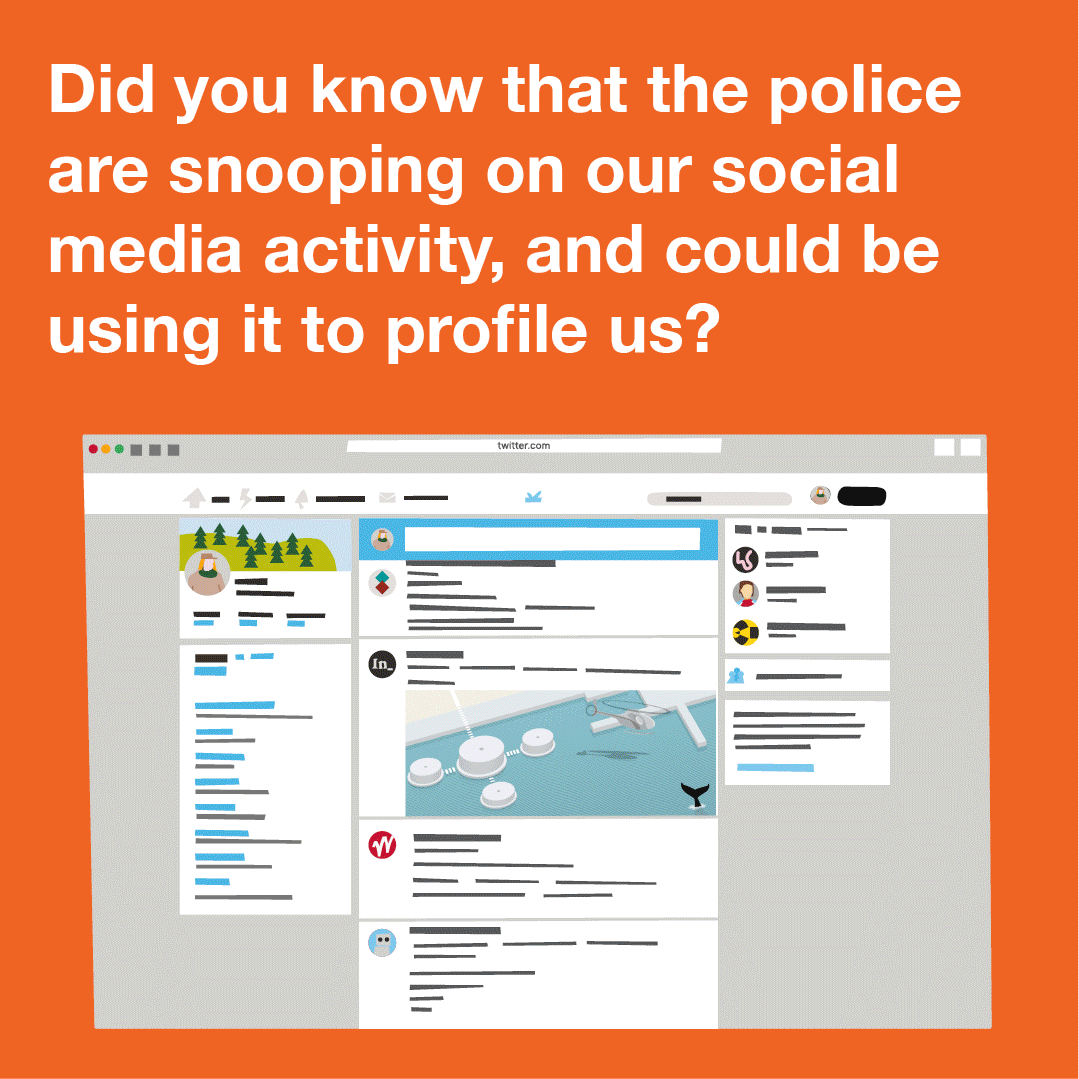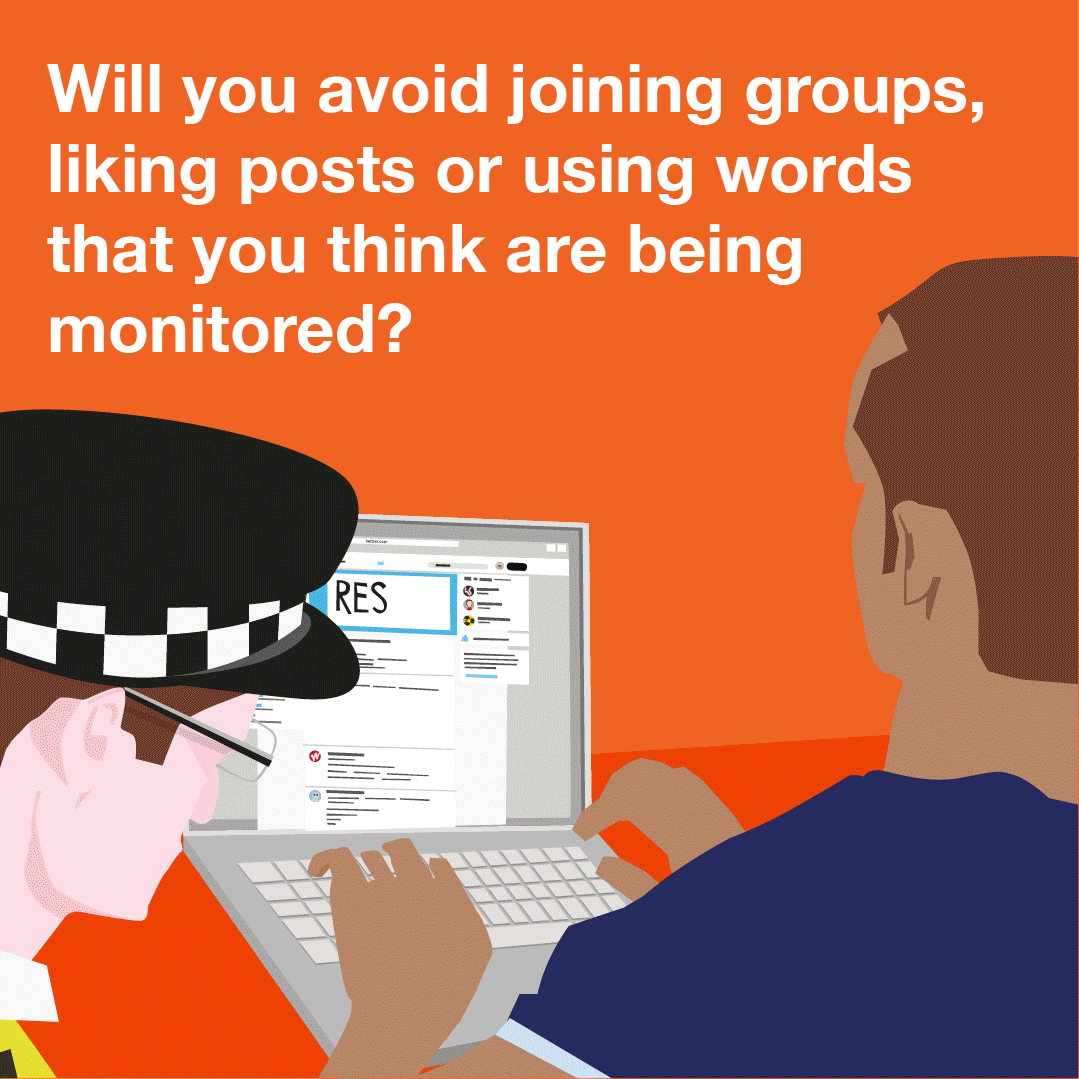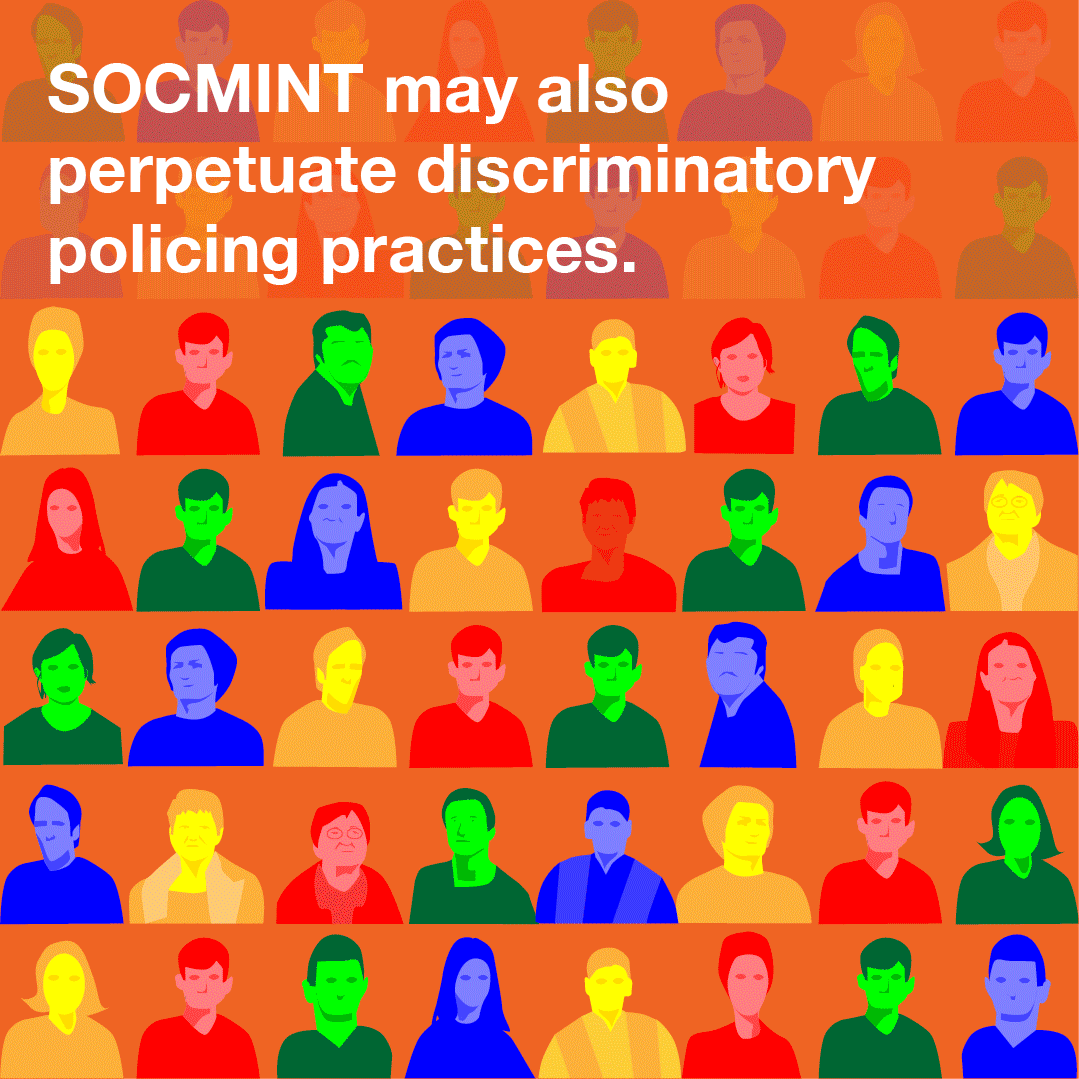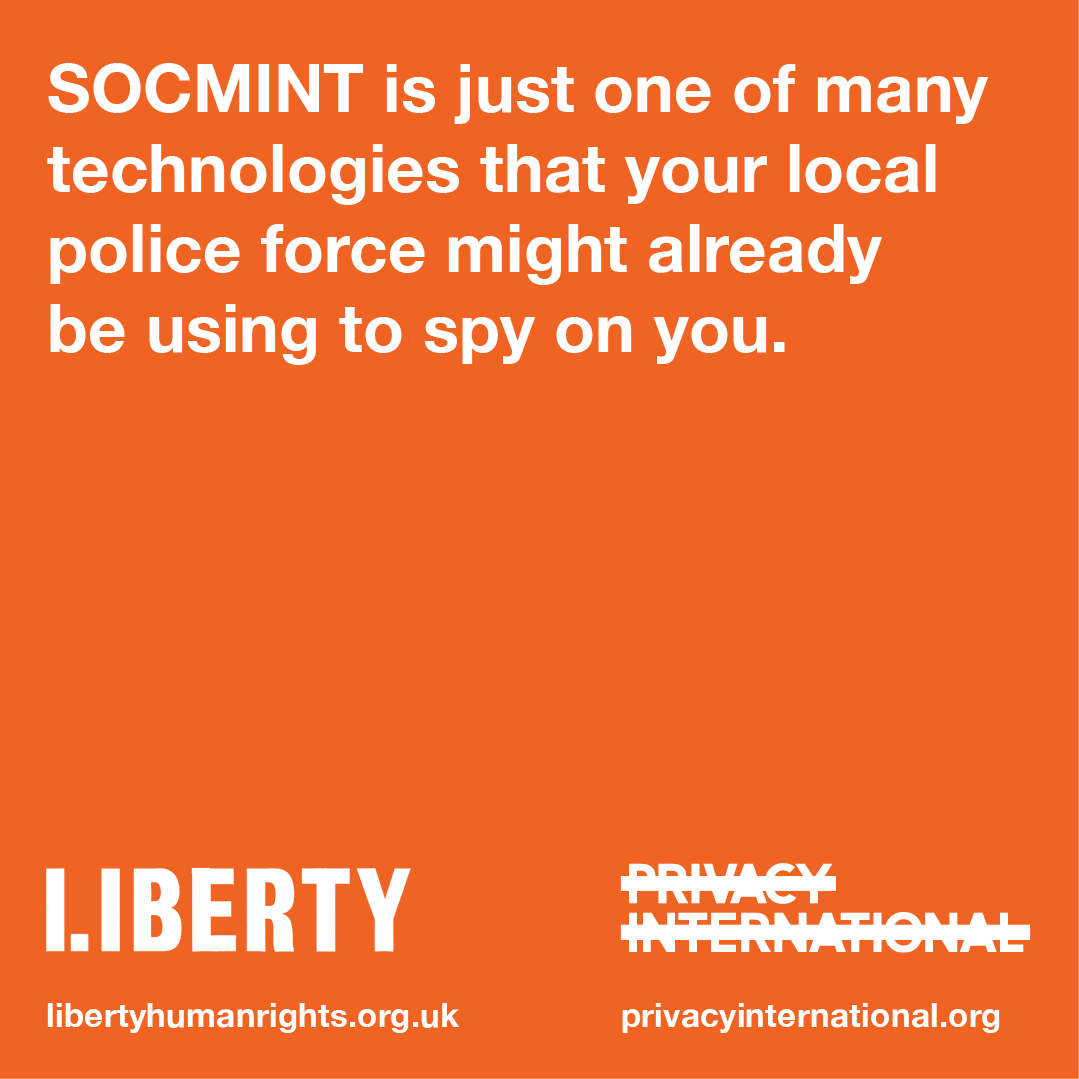
Content Type: Explainer graphic
You can also read a more detailed explainer about social media intelligence (SOCMINT) here.