Search
Content type: Case Study
On 3 December 2015, four masked men in plainclothes arrested Isnina Musa Sheikh in broad daylight (at around 1 p.m.) as she served customers at her food kiosk in Mandera town, in the North East of Kenya, Human Rights Watch reported. The men didn’t identify themselves but they were carrying pistols and M16 assault rifles, commonly used by Kenyan defence forces and the cars that took her away had their insignia on the doors. Isnina’s body was discovered three days later in a shallow grave about…
Content type: Case Study
The prohibition against torture is absolute. There are no exceptional circumstances whatsoever which can be used to justify torture.
And yet, torture is still being carried out by state officials around the world, driven by states’ ability to surveil dissidents, and intercept their communications.
In 2007, French technology firm Amesys (a subsidiary of Bull) supplied sophisticated communications surveillance systems to the Libyan intelligence services. The systems allegedly permitted the…
Content type: Case Study
In the Xingjiang region of Western China, surveillance is being used to facilitate the government’s persecution of 8.6million Uighur Muslims.
Nurjamal Atawula, a Uighur woman, described how, in early 2016, police began regularly searching her home and calling her husband into the police station, as a result of his WeChat activity.
WeChat is a Chinese multi-purpose messaging, social media and mobile payment app. As of 2013, it was being used by around 1million Uighurs, but in 2014 WeChat was…
Content type: Case Study
The way digital technologies are deployed has radically influenced the distribution of power in our societies. Digital information can be created, transmitted, stored and distributed far more easily and cheaply than ever before, on a scale that was previously unimaginable. This information is power in the hands of those that know how to use it. Governments and companies alike have been racing to occupy as much space as possible, increasing their surveillance and their knowledge about each and…
Content type: News & Analysis
On 24 October 2019, the Swedish government submitted a new draft proposal to give its law enforcement broad hacking powers. On 18 November 2019, the Legal Council (“Lagråd”), an advisory body assessing the constitutionality of laws, approved the draft proposal.
Privacy International believes that even where governments conduct hacking in connection with legitimate activities, such as gathering evidence in a criminal investigation, they may struggle to demonstrate that hacking as…
Content type: News & Analysis
*Photo by Michelle Ding on Unsplash
Pat Finucane was killed in Belfast in 1989. As he and his family ate Sunday dinner, loyalist paramilitaries broke in and shot Pat, a high profile solicitor, in front of his wife and children.
The Report of the Patrick Finucane Review in 2012 expressed “significant doubt as to whether Patrick Finucane would have been murdered by the UDA [Ulster Defence Association] had it not been for the different strands of involvement by the…
Content type: Long Read
*Photo by Kristina Flour on Unsplash
The British government needs to provide assurances that MI5’s secret policy does not authorise people to commit serious human rights violations or cover up of such crimes
Privacy International, along Reprieve, the Committee on the Administration of Justice, and the Pat Finucane Centre, is challenging the secret policy of MI5 to authorise or enable its so called “agents” (not MI5 officials) to commit crimes here in the UK.
So far we have discovered…
Content type: Advocacy
In this submission, Privacy International aims to provide the Office of the UN High Commissioner for Human Rights with information on how surveillance technologies are affecting the right to peaceful protests in new and often unregulated ways.
Based on Privacy International’s research, we provide observations, regarding the following:
the relationship between peaceful protests and the right to privacy;
the impact of new surveillance technologies in the context of peaceful protests…
Content type: News & Analysis
Photo: The European Union
“Border Externalisation”, the transfer of border controls to foreign countries, has in the last few years become the main instrument through which the European Union seeks to stop migratory flows to Europe. Similar to the strategy being implemented under Trump’s administration, it relies on utilising modern technology, training, and equipping authorities in third countries to export the border far beyond its shores.
It is enabled by the adoption…
Content type: Examples
A 17-year-old Palestinian resident of Lebanon, Ismail B. Ajjawi, was deported shortly after he arrived at Boston Airport, where he was due to start attending Harvard University the following week.
Immigration officers subjected him to hours of questioning — at one point leaving to search his phone and computer — according to a written statement by Ajjawi. According to the student, his visa was revoked because of content posted by some social media contacts.
The student alleges that…
Content type: Examples
In October 2018, the Singapore-based startup LenddoEFL was one of a group of microfinance startups aimed at the developing world that used non-traditional types of data such as behavioural traits and smartphone habits for credit scoring. Lenddo's algorithm uses numerous data points, including the number of words a person uses in email subject lines, the percentage of photos in a smartphone's library that were taken with a front-facing camera, and whether they regularly use financial apps on…
Content type: Examples
In 2017, US Immigration & Customs Enforcement (ICE) announced that it would seek to use artificial intelligence to automatically evaluate the probability of a prospective immigrant “becoming a positively contributing member of society.” In a letter to acting Department of Homeland Security Secretary Elaine Duke, a group of 54 concerned computer scientists, engineers, mathematicians, and researchers objected to ICE’s proposal and demanded that ICE abandon this approach because it would be…
Content type: News & Analysis
Today, the British Health Secretary Matt Hancock announced a partnership between the NHS and Amazon to use the NHS’s website content as the source for the answer given to medical question, such as “Alexa, how do I treat a migraine?”
While we welcome Amazon’s use of a trusted source of information for medical queries, we are however extremely concerned about the nature and the implications of this partnership. Amazon is a company with a worrying track record when it comes to the way they…
Content type: Advocacy
Refugees are among the most vulnerable people in the world. From the moment they flee their homes, as they pass through 'temporary' places such as refugee camps and detention centres to their 'final' destinations, they are continuously exposed to threats. In the digital age, these threats are increasingly being driven by the processing of vast amounts of highly sensitive personal data: from enrollment and registration processes needed for them to access services, to their identification and…
Content type: Examples
In February 2019 Google engineers announced that they had created faster, more efficient encryption system that could function on less-expensive Android phones that were too low-powered to implement existing full-device encryption. The scheme, known as Adiantum, uses established and well-vetted encryption tools and principles. Android has required smartphones to support encryption since 2015's version 6, but low-end devices were exempt because of the performance hit. It will now be up to device…
Content type: Long Read
Imagine that every time you want to attend a march, religious event, political meeting, protest, or public rally, you must share deeply personal information with police and intelligence agencies, even when they have no reason to suspect you of wrongdoing.
First, you need to go to the police to register; have your photo taken for a biometric database; share the contacts of your family, friends, and colleagues; disclose your finances, health records, lifestyle choices, relationship status, and…
Content type: News & Analysis
Protest movements throughout history have helped to shape the world we know today. From the suffragettes to the civil rights movement, and to contemporary movements such as those focusing on LGBTIQ+ rights, protests have become a vital way for many, who feel powerless otherwise, to have their voices heard.
But now, making the decision to attend a protest comes with consequences that you may very well be unaware of. This is because policing and security services, always hungry in their quest to…
Content type: News & Analysis
According to the International Organization for Migration, an estimated 258 million people are international migrants – that is, someone who changes their country of usual residence, That’s one in every 30 people on earth.
These unprecedented movements levels show no sign of slowing down. It is predicted that by 2050, there will be 450 million migrants across the world.
Nowadays, it is politically acceptable to demonise migrants, and countless leaders have spewed divisive and xenophobic…
Content type: Long Read
(In order to click the hyperlinks in the explainer below, please download the pdf version at the bottom of the page).
Content type: News & Analysis
Planning and participating in peaceful protests against governments or non-state actors’ policies and practices requires the capacity of individuals to communicate confidentially without unlawful interference. From protests in support of LGBTI rights to protests against specific projects that undermine local communities’ wellbeing, these movements would not have been possible without the ability to exchange ideas and develop plans in private spaces.
Unlawful interference with…
Content type: Long Read
(In order to click the hyperlinks in the explainer below, please download the pdf version at the bottom of the page).
Content type: Explainer graphic
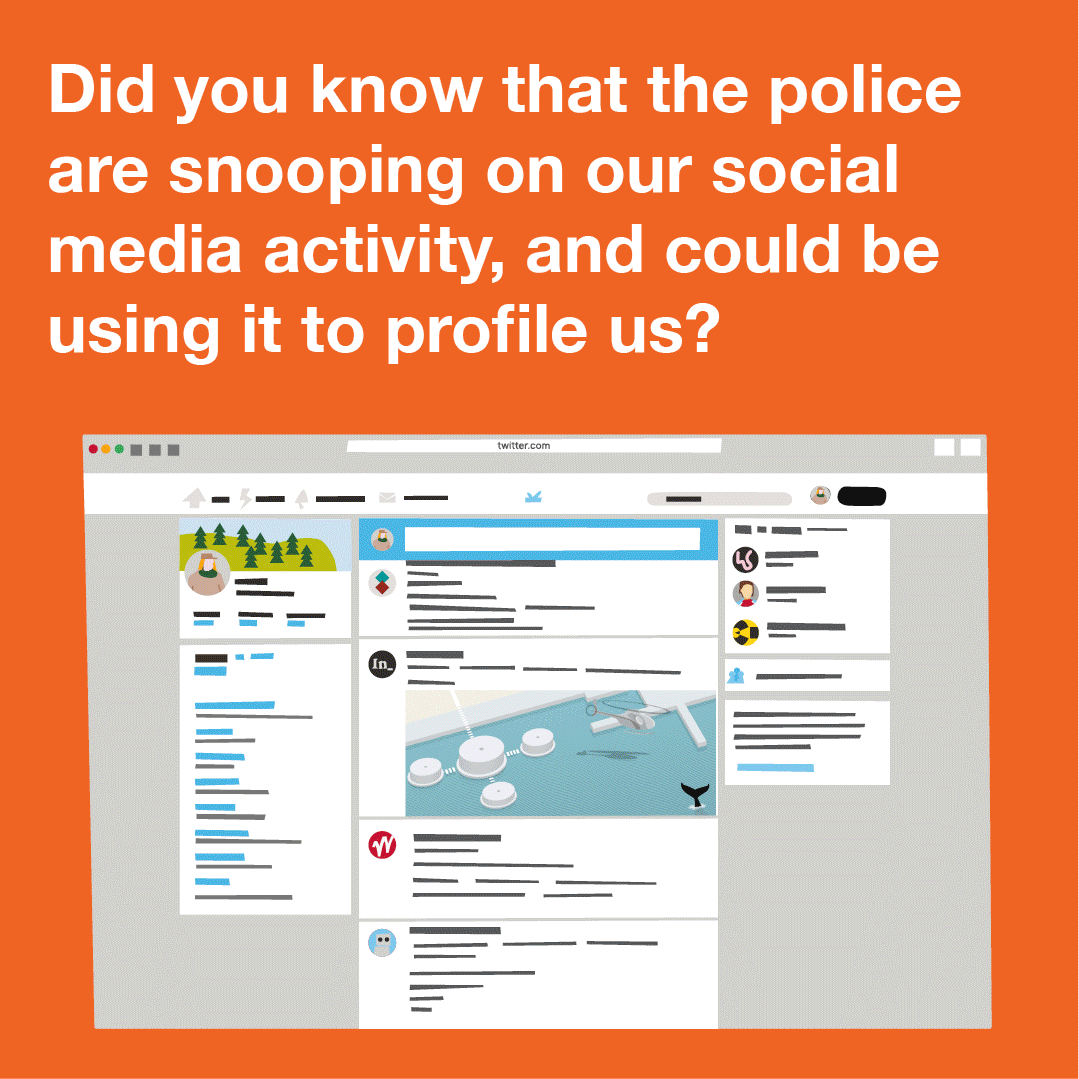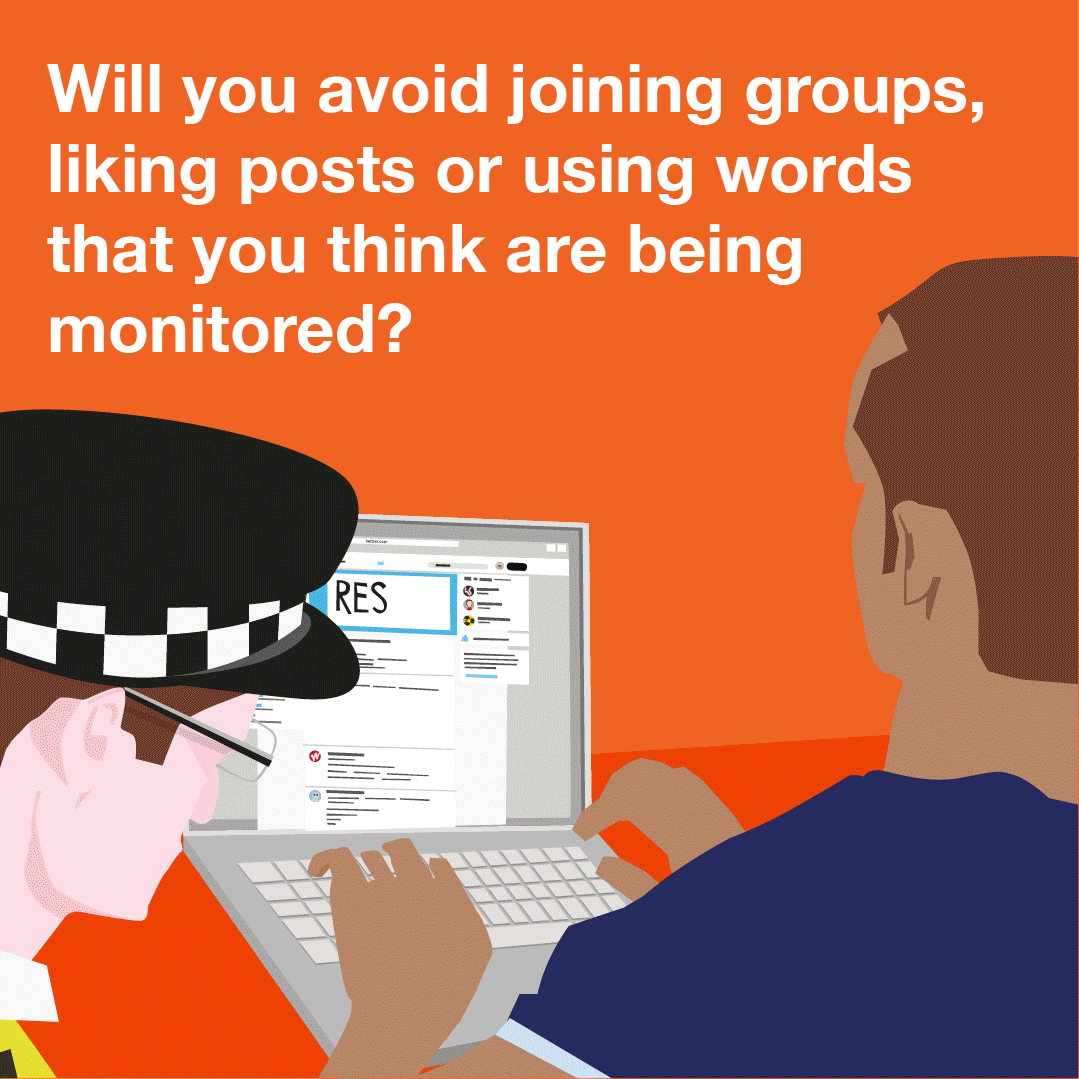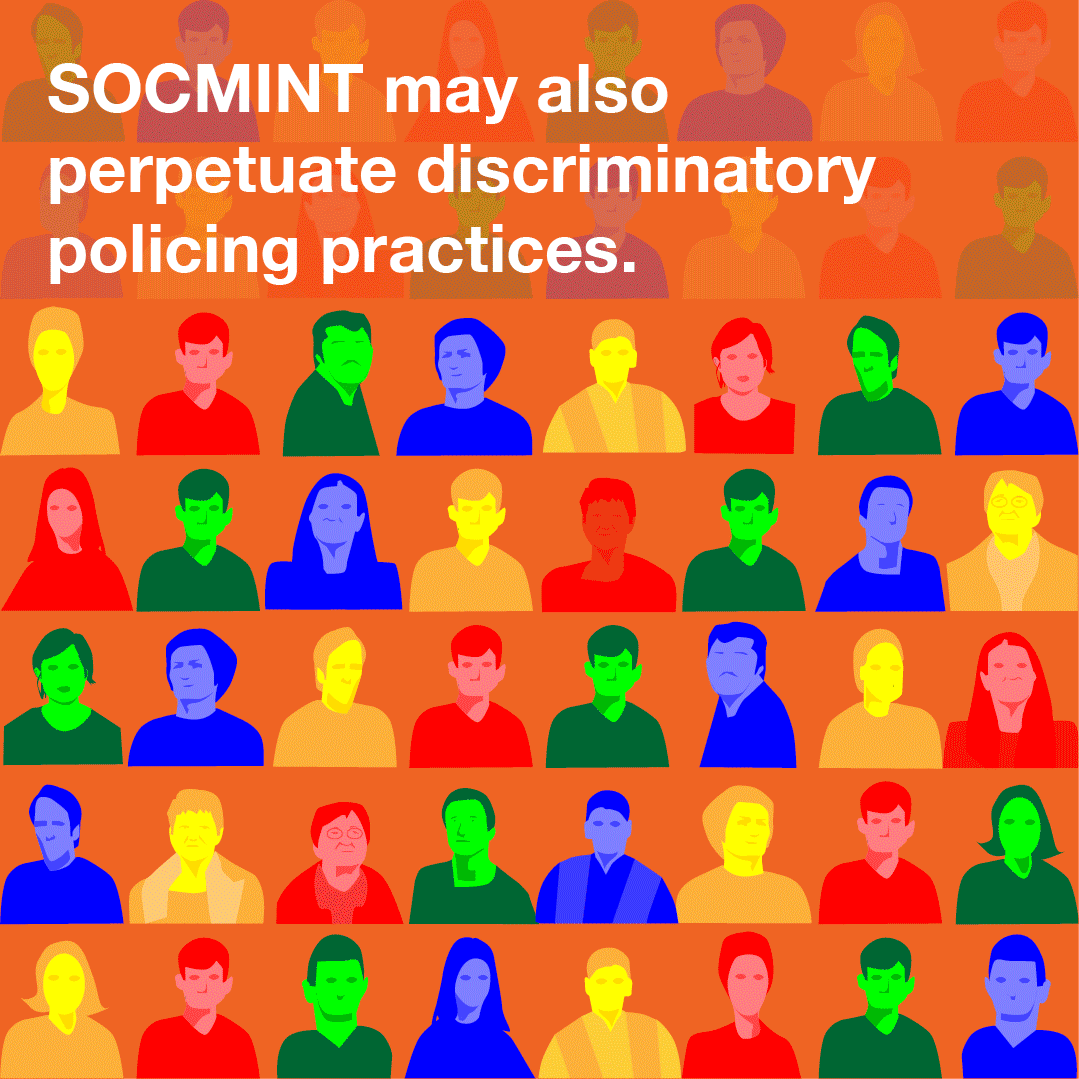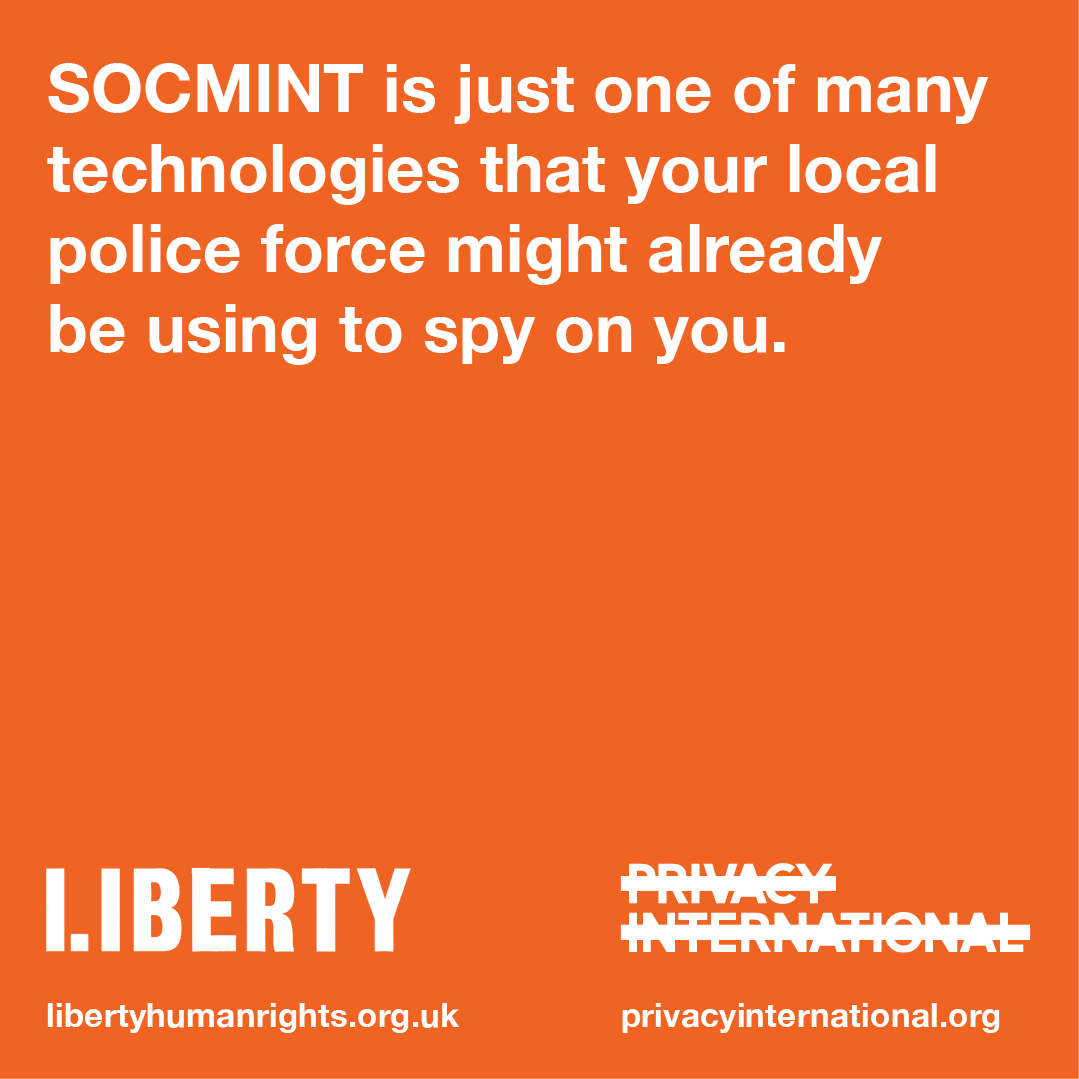
You can also read a more detailed explainer about social media intelligence (SOCMINT) here.
Content type: Explainer graphic
You can also read a more detailed explainer about facial recognition cameras here.
Content type: Explainer graphic
You can also read a more detailed explainer about IMSI catchers here.
Content type: Examples
In July 2018, Facebook announced it was investigating whether the Boston-based company Crimson Hexagon had violated the company's policies on surveillance. Crimson Hexagon markets itself as offering "consumer insights". Its customers include a Russian non-profit with ties to the Kremlin, and multiple US government agencies. After pressure from civil liberties groups, Facebook put a policy in place in March 2017 barring the use of members' data for the purposes of government surveillance.…