Advanced Search
Content Type: Report
In this new briefing, we identify the most significant concerns on the UN Countering Terrorist Travel Programme (CTTP), and put forward a range of recommendations to mitigate some of the human rights risks associated with the surveillance of travellers. We based our briefing on publicly available information and our own research, outlining the purposes and activities of this UN programme. We shared a draft of this briefing with the United Nations Office of Counter- Terrorism (OCT), which…
Content Type: Report
With this report, we shed light on the due process implications of the blanket and indiscriminate surveillance of protesters, activists, and human rights defenders participating in protests. We demonstrate that information gathered through the surveillance of protests is being used in criminal proceedings against activists, protesters, and human rights defenders. We also also show that when this information is being admitted as evidence in criminal proceedings it undermines the right to fair…
Content Type: Long Read
Our briefing, “When Spiders Share Webs: The creeping expansion of INTERPOL’s interoperable policing and biometrics entrench externalised EU borders in West Africa”, explores the concerning human rights implications of the use of interoperable data-driven policing capabilities and biometric technologies in West African countries rolled out by the International Criminal Police Organisation (INTERPOL)’s European Union (EU)-funded West African Police Information System (WAPIS) programme. We make a…
Content Type: Report
Over the past years, data retention regulation imposing generalised and indiscriminate data retention obligations to telecommunication companies and Internet service provides has been introduced in various jurisdictions across the world. As the data retention practices across the world have evolved this new report is an attempt to shed some light on the current state of affairs in data retention regulation across ten key jurisdictions. Privacy International has consulted with human…
Content Type: Report
The methodology employed for this report consists primarily of in-depth interviews held with grassroots political workers and representatives of collectives. The researchers interviewed 14 individuals from various social justice causes such as womens’ rights, climate change, transgender rights, students’ rights and the right to universal internet access in Pakistan. The experiences they have shared with the interviewers along with the real-time developments in the country’s law and order…
Content Type: Report
This policy paper seeks to determine the potential for the existing international private military and security companies (PMSC) regulatory framework to support more effective regulation of surveillance services provided by the private sector.In order to achieve this, and given that this paper addresses an issue that is at the intersection of two domains, it seeks to establish a common language and terminology between security sector governance and surveillance practitioners.In…
Content Type: Long Read
IntroductionData about our health reveals some of the most sensitive, intimate - and potentially embarrassing - information about who we are. Confidentiality is, and has always been, at the very heart of medical ethics. People need to be able to trust their doctors, nurses and other healthcare providers so that they are not afraid to tell them something important about their health for fear of shame, judgement or social exclusion.It’s no surprise then that data protection regimes around…
Content Type: Long Read
The rise of racist and xenophobic narratives around the world has led to a ramping up of brutal migration control policies. Indefinite detention, pushbacks of boats at sea, or deportation for offshore processing of asylum claims all now form part of the arsenal deployed by some governments to “appear tough” on and provide "solutions" to immigration. A stark example is the UK’s “hostile environment” policy, announced 10 years ago by then Home Secretary Theresa May and designed to deter migrants…
Content Type: Long Read
The final report on the 2022 Kenyan election is the result of a collaboration with the Carter Center as part of a joint pre-election assessment focussing on the use of technology in the run up to and during the Kenyan election which took place 9 August. The final report, published this month, follows our preliminary statement of September 2022.
Below we set out a few key observations in connection with the use of data and technology, as well as some of the key data protection incidents.
Key…
Content Type: Case Study
This piece was written by Privacy International, based on publicly available information and on research by our partners at Hiperderecho
Overview
The Documento Nacional de Identidad (DNI) is the personal ID card recognised by the Peruvian State in any situation where a person might have to identify themselves, be it in an administrative, judicial, civil, or commercial context. The DNI also grants its holder the right to vote.
The DNI issuing and overseeing body is the Registro Nacional de…
Content Type: Report
PI has been fighting against police using intrusive & disproportionate surveillance technologies at protests around the world for years. Unregulated surveillance and indiscriminate intrusions on our privacy have a chilling effect on the right to freedom of assembly.
We've fought to uncover the types of technologies that police secretly deploy at protests, and we have detailed how protesters around the world can try to protect their intimate and sensitive data from being captured by the…
Content Type: Long Read
The rise of the gig-economy, a way of working relying on short term contracts and temporary jobs rather than on an employed workforce, has enabled the growth of a number of companies over the last few years. But without the rights that comes with full employment, gig economy workers today don't have access to essential protections.
In 2021, PI worked with ACDU and Worker Info Exchange to shed a light on the power imbalance between workers and gig economy platforms, exposing how workers find…
Content Type: Report
In the months following the beginning of the Covid-19 pandemic, more than half the world’s countries enacted emergency measures. With these measures came an increase in executive powers, a suspension of the rule of law, and an upsurge in security protocols – with subsequent impacts on fundamental human rights. Within this broader context, we have seen a rapid and unprecedented scaling up of governments’ use of technologies to enable widespread surveillance. Surveillance technologies exacerbated…
Content Type: Long Read
Introduction
India’s educational system is the largest in the world, with over 250 million students, 50% of whom attend publicly administered schools.
The autonomy given by the Indian Constitution to the 28 states and 8 union territories means that the right to education is implemented quite differently in each one, respecting culture, language, and other local specificities. Educational policies are suggested at the national level by various autonomous agencies and states can implement them in…
Content Type: Report
Introduction
Several policy initiatives are in progress at the EU level. They seek to address the sustainability of connected devices such as smartphones, tablets and smart speakers. While initiatives to extend the useful life of hardware are important, software must not be ignored. Almost any digital device with which we interact today relies on software to function, which acts as a set of instructions that tells the hardware what to do. From smart thermostats to smart speakers, to our…
Content Type: Press release
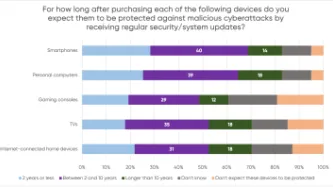
A YouGov survey commissioned by PI shows that consumers expect their smartphones, computers, smart TVs and gaming consoles to receive security updates for a much longer period than what several manufacturers actually provide, leaving consumers with expensive tech that is vulnerable to cyberattacks.
The majority of consumers in the survey assumed their devices would be protected beyond two years, but current industry practices fail to meet these expectations. PI investigated the software…
Content Type: Report
End-to-end encryption (E2EE) contributes significantly to security and privacy. For that reason, PI has long been in favour of the deployment of robust E2EE.Encryption is a way of securing digital communications using mathematical algorithms that protect the content of a communication while in transmission or storage. It has become essential to our modern digital communications, from personal emails to bank transactions. End-to-end encryption is a form of encryption that is even more private.…
Content Type: Long Read
Introduction
In response to the unprecedented social, economic, and public health threats posed by the Covid-19 pandemic, the World Bank financed at least 232 "Covid-19 Response" projects. The projects were implemented across countries the World Bank classifies as middle and low-income.
This article will focus on eight (8) Covid-19 Response projects which sought to deliver social assistance to individuals and families on a "non-contributory" basis (this means that the intended beneficiaries…
Content Type: Long Read
The global COVID-19 health crisis not only induced a public health crisis, but has led to severe social, economic and educational crises which have laid bare any pre-existing gaps in social protection policies and frameworks. Measures identified as necessary for an effective public health response such as lockdowns have impacted billions workers and people's ability to sustain their livelihood worldwide, with countries seeing unprecedented levels of applications for welfare benefits support,…
Content Type: Long Read
Imagine your performance at work was assessed directly from the amount of e-mails sent, the amount of time consumed editing a document, or the time spent in meetings or even moving your mouse. This may sound ludicrous but your boss might be doing exactly that. There are more and more stories emerging of people being called into meetings to justify gaps in their work only to find out their boss had been watching them work without their knowledge.
The Covid-19 global pandemic has reshuffled the…
Content Type: Report
Privacy International’s submissions for the Independent Chief Inspector of Borders and Immigration inspection of the Home Office Satellite Tracking Service Programme
The Home Office have introduced 24/7 electronic monitoring and collection of the location data of migrants via GPS ankle tags. This seismic change cannot be overstated. The use of GPS tags and intention to use location data, kept for six years after the tag is removed, in immigration decision-making goes far beyond the mere…
Content Type: Report
El informe se basa en investigación documental y empírica (cualitativa y cuantitativa) realizada por Privacy International (PI) en 2021. Más concretamente, PI envió una encuesta a varios reguladores antimonopolio y a organizaciones de la sociedad civil con sede y/o que operan en diversas partes del mundo.
Las preguntas planteadas a los reguladores y a la sociedad civil versaron sobre su trabajo en la economía digital. Se preguntó a los reguladores y a las OSC si incorporaban consideraciones…
Content Type: Report
The report builds on both desk and empirical (qualitative and quantitative) research that was carried out by Privacy International (PI) in 2021. Specifically, PI sent out a survey to several antitrust regulators and CSOs based and/or operating in various parts of the world. The questions posed to regulators and civil society revolved around their work in the digital economy. Regulators and CSOs were asked to comment on whether and how personal data considerations were incorporated into their…
Content Type: Report
This briefing takes a look at the private intelligence industry, a collection of private detectives, corporate intel firms, and PR agencies working for clients around the world that have made London their hub.
Often staffed by ex-spooks, and promising complete secrecy, little is known about them. But reports over the years have exposed their operations, including things like hacking and targeting of anti-corruption officials, spying on peaceful environment activists, and running fake '…
Content Type: Report
Democratic engagement is increasingly mediated by digital technology, from campaigning to election results transmission. A key example of the application of new technologies to democratic processes is the growing practice of micro-targeting in political campaigning around the globe, including Colombia.
In 2018, the mayor of Bogotá, Enrique Peñalosa, was accused of hiring Cambridge Analytica during his 2015 election campaign. That same year, Cambridge Analytica’s former director acknowledged…
Content Type: Long Read
In a previous article, we mapped the influence of the Chinese company Huawei across the world and how their sales of smart city infrastructures are contributing to the reshaping of our public space.
We should be alarmed by some of their product deployments – such as the installation of facial recognition technologies in countries with concerning human rights records. But also the deployments of facial recognition technology in countries without strong data protection laws are as such…
Content Type: Long Read
The smart city market is booming. And with a booming market comes companies that are profiting and reshaping our public space, like the Chinese tech company Huawei.
While the term ‘Smart City’ is a broad one that encompasses many different initiatives, some with little to no impact on our privacy and other rights. Certain issues are nevertheless recurrent: the lack of transparency around public-private partnerships, the absence of consultation, and the appetite for a “tech quick fix…