A technical look at Phone Extraction

In this piece we examine mobile phone extraction, relying on publicly available information and Privacy International’s experience from conducting mobile phone extraction using a Cellebrite UFED Touch 2. We welcome input from experts in the field. This is a rapidly developing area. Just as new security features are announced for phones, so too new methods to extract data are found.
[All references can be found in the pdf version below.]
General explanation of mobile phone extraction
Mobile Phone Extraction technologies, known also as mobile forensics, entails the physical connection of the mobile device that is to be analysed and a device that extracts, analyses and presents the data contained on the phone. Whilst forensics experts, hackers and those selling spyware may be able to access and extract data, we look at a number of the most well-known commercial companies who sell their products to law enforcement, such as Cellebrite, Oxygen Forensic Detective, and MSAB.
Android and iOS
Our analysis focuses on Android and iOS when looking at extractive technologies. Android is the leading operating system for phones worldwide. “According to IDC, in the first quarter of 2017, Android dominated the industry with an 85% market share.” iOS leads the way in relation to security and presents the biggest forensic challenge. “...without the passcode we can hardly extract anything from the modern iOS device.” For example iOS’s USB restricted mode, which first appeared in iOS 11.4.1, disabled USB communications after one hour of the last unlock which causes issues of those conducting an extraction. As USB restricted mode develops with iOS releases, for many in the world of forensics it is simply a challenge to overcome. Mobile phone extraction could be characterised as an arms race, where vendors are constantly seeking to overcome obstacles of increased phone security.
“We want to start with the bad news: if you are examining an iPhone that runs iOS 8 or newer … chances to unlock it are not good at all...With iOS 11 this problem becomes even more severe - even if the device under examination is not passcode-protected, the examiner will need the passcode anyway as it must be entered to confirm the trust between the device and your workstation.”
An important differentiator between iOS and Android in terms of forensics capabilities is that whilst Apple can push updates directly to their users, patching vulnerabilities and exploits, Android users are predominantly reliant on the manufacturer and carrier to provide update. This causes many Android phones to be running older versions of the operating systems which means various forms of extraction are viable. “The variety of the operating system versions and the hardware platforms on which they are used provide a wide range of data extraction methods. ”
Vulnerabilities
In evaluating MPE technologies, this project looks at some of the vulnerabilities used to obtain data, particularly for Android phones, such as the use of Emergency Download Mode for devices with the Qualcomm chipset.
What current technologies are used to access, extract and analyse data from mobile phones?
“Mobile device forensics is likely the most rapidly advancing discipline that digital forensics has ever seen or ever will see, primarily because of the rapidly changing environment of the actual devices. Device operating systems have become more advanced, and the storage capacity on the current devices is astronomical. Today’s devices are mobile computing platforms, but accessing the data contained on these devices is much more difficult than accessing data from any other digital device.”
Accessing and extracting data from phones is nothing new. However, as the volume of data on phones explodes and “the mobile landscape is changing each passing day” the ability to access, extract and analyse this data is increasingly difficult and complex. Techniques vary depending on the hardware and software of a phone, from the chipset (Qualcomm, MediaTek) to the operating system version. “Extracting data from a mobile device is half the battle. The operating system, security features, and type of smartphone will determine the amount of access you have to the data.”
Encryption and other security measures present significant challenges.
“As mobile technology continues to mature, and the amount security and encryption continues to strengthen, it’s becoming more of a challenge to know how to access data on smartphones that are password-protected. On top of the encryption challenge is the manufacturing variants that can create different roadblocks along the way.”
There are three generic types of extraction: logical, file system and physical, which provide a framework to consider extraction technologies. No one technology can access and extract all data from all phones, and no one type of extraction is guaranteed to be successful. As acknowledged by MobilEdit, a phone forensics company, when commenting on the US National Institute of Standards and Technology (NIST) test results for mobile device acquisition:
“Tests have also shown that there are significant differences in results between individual data types across the competitive tools tested. Each tool was able to demonstrate certain strengths over the others, and there is no single tool that demonstrated superiority in all testing categories. Our conclusion is that there is a significant increase in the success rate when performing a cross-reference tool analysis. In the real world, when there is a case, each piece of evidence matters. With a combination of tools you can get up to 89.6% overall success rate.”
Physical acquisition is generally the preferred method. As it extracts the raw data at a binary level, from the devices storage. Even if this is possible there is a view that “A logical acquisition should always be obtained as it may contain only the parsed data and provide pointers to examine the raw memory image.”
Factors such as the status of the mobile device will determine whether logical or physical extraction is attempted. “The type of examination is contingent on the device’s power status and whether the device is locked, password protected, or disabled (disassembled or broken) ...Not all mobile devices can be collected physically. An iPhone 5 to X, for example, cannot be collected physically using non-invasive methods.”
The reality of carrying out mobile phone extraction is that you will often have to try all types of extraction that the tool you have offers. However, the ability to do this will be limited by time, resources and expertise.
A developing area is Cloud extraction which we look at in more detail in a separate article. This development makes for disturbing reading, as we grasp how much is held in remote servers and accessible to those with no forensic skill but the money to pay for push button technologies that can grab it all. Cloud extraction, a leap from what is on the phone to what is accessible from it, is a reaction to encryption and device locks that make traditional mobile phone forensics hard if not impossible and a response to the volume of information stored in the Cloud.
“Today’s digital investigators should not ignore the significance of the data stored in various cloud services. Without cloud data, the information that can be gathered from traditional sources (such as mobile device, flash media, or computer) is limited, inconclusive, or simply unobtainable.”
Once data is extracted there are some impressive products on offer to read and analyse extracted data. Increasingly these are marketed with artificial intelligence capabilities to assist investigators.
Analysis: Access & extraction: physical, logical, file system
First an analysis of the three main types of extraction: logical, file system and physical and the tools used to carry these out. These methods vary in technicality and the type and volume of data they can extract.
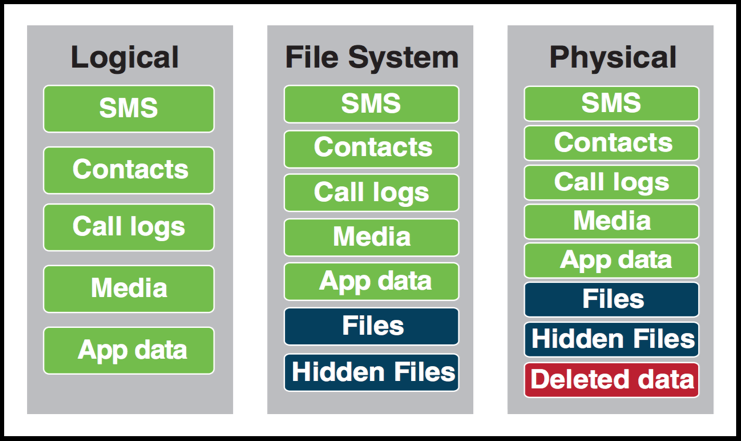
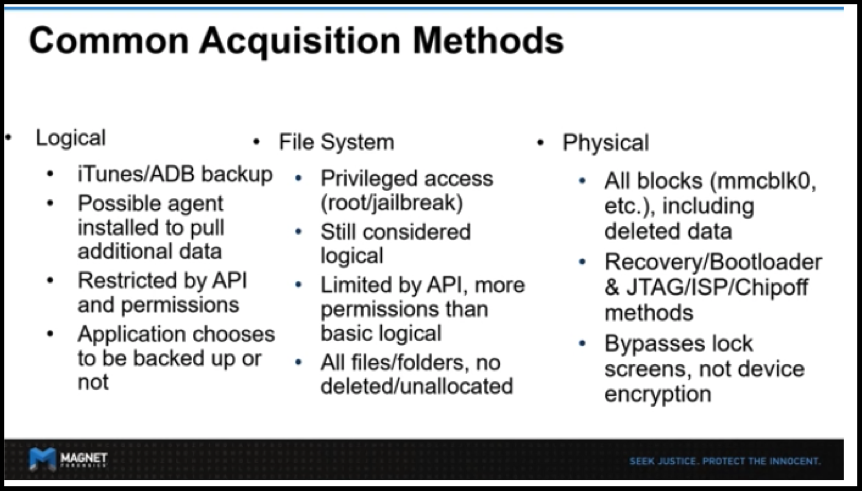
Under each generic method, companies may differ on the way they achieve the extraction. As set out in a slide from Magnet Forensics (below), a logical extraction can be achieved via iTunes/ADB backup or installing an agent to pull additional data; a File System using privileged access such as root or jailbreak; and Physical using recovery or bootloader methods.
There are other invasive methods to extract data from phones. JTAG (Joint Test Action Group), ISP (In System Programming) and Chip-off (or any associated hardware forensic methodology, such as inter-chip communication interception - If you are dismantling the device, you may be able to intercept the data as it travels from one microcontroller to another/processor, for example I2C or SPI, bypassing a software defined security model) are more reliant on forensics skill as opposed to the newest technology and thus are mentioned briefly.
JTAG is a method named after the industry standard for verifying designs and testing printed circuit boards after manufacture. It involves connecting to the Standard Test Port to transfer raw data from memory chips. “The JTAG technique involves probing the JTAG Test Access Ports and soldering connectors to the JTAG ports in order to read data from the device memory.” ISP “is the practice of connecting to an eMMC or eMCP flash memory chip for the purpose of downloading a device’s complete memory content”. Chip-off is a destructive method, which is based on the removing of memory chip from system board and a chip reader is used to extract data stored.
Finally, manual extraction which does not require sophisticated tools and:
“...involves simply scrolling through the data on the device and viewing the data on the phone directly through the use of the device’s keypad or touchscreen. The information discovered is then photographically documented... At this level, it is not possible to recover deleted information and grab all the data.”

Logical extraction
“Logical acquisition is about extracting the logical storage objects, such as files and directories that reside on the filesystem. Logical acquisition of mobile phones is performed using the device manufacturer application programming interface to synchronize the phone’s contents with a computer. Many of the forensic tools perform a logical acquisition...A logical acquisition is easy to perform and only recovers the files on a mobile phone and does not recover data contained in unallocated space.“
What is it?
Out of the three types of extraction, logical is seen as the quickest, least intrusive, but most limited. It creates a copy of the user accessible files such as phonebook, calls, messages, some app data and other data you might expect from an iTunes or Android backup. i.e. what you can see if you manually examine each screen on the device.
MSAB, which describes itself as ‘a pioneer in forensic technology for mobile device examination” markets their XRY Logical as “our entry-level solution for forensic investigators and the starting point for our license options”.
“XRY Logical enables the user to conduct quick extractions (of iTunes backup, Android backup, Android Agent) and is geared toward “pump-and-dump” examinations.”

Logical extraction may exclude data from certain apps if those apps do not backup into the files which form part of the extraction e.g. the default folder. To access these apps you would need access to the file system.
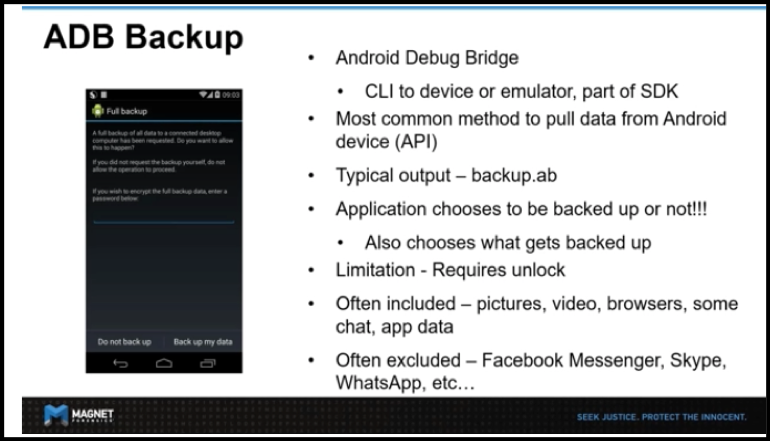
“Note for Android Devices: Non-system Android apps can choose to opt-out of the backup (e.g. WhatsApp). If the app manufacturer selects, then no app data is stored in the backup; a method commonly used for logical data recovery from mobile devices.”
Thus, you obtain only that which is available through a vendor’s API. i.e. the phone can restrict what you can access. However, for Android phones, it may be possible to obtain app data by downgrading the target app to an older version where adb backup is allowed. The ability to do this is reportedly blocked in newer versions of Android. Although Cellebrite UFED 7.16 update on APK Downgrade method states it “enables access to file system data from more than 40 applications on Android device running version 6.0 and above.”
Logical extractions typically do not include a full bit-by-bit copy of the data or recover deleted data. However, it may be possible to recover deleted records including SMS, chats and browsing history if SQLite databases are used to store the data using for example Cellebrite’s SQLite Wizard. As noted by Reiber (2019:159), “within a subset of devices such as iOS and Android devices, a logical file extraction can often contain deleted data.”
How does it work?
Logical extraction involves “connecting the mobile device to forensic hardware or to a forensic workstation via a USB cable, a RJ-45 cable, infrared or Bluetooth”. Once the phone is connected, the forensic tool “initiates a command and sends it to the device, which is then interpreted by the device processor.” i.e. the forensic tools communicate with the operating system of the mobile device. The data requested as a result of the use of proprietary protocols and queries is:
“…received from the device’s memory and sent back to the forensic workstation. Later, the examiner can review the data. Most of the forensic tools currently available work at this level of the classification system.”
Using the Application Programming Interface (“API”), is one way to carry out logical extraction. Cellebrite, a leading forensics company popular with government agencies, states “From a technical standpoint, API-based logical extraction is straightforward to implement, and the results are provided in a readable format.”
Cellebrite’s UFED Touch (hardware with UFED software) and UFED 4PC (software installed on a computer) work by communicating with the operating system of a device using the API.
“Logical extraction of data is performed, for the most part, through a designated API, available from the device vendor. Just as the API allows commercial third-party apps to communicate with the device OS, it also enables forensically sound data extraction...Upon connection, the UFED loads the relevant vendor API to the device. The UFED then makes read-only API calls to request data from the phone. The phone replies to valid API requests to extract designated content items such as text messages (SMS), phonebook entries, pictures, etc.”
Logical extraction on an iPhone using a Cellebrite UFED Touch 2 works similarly to how iTunes or iCloud might take a backup, it displays on the phone screen the various prompts for the data being extracted, for example ‘Backup Call Data” (Yes/No).
Some forensics tools install an App or agent onto the device to try and pull additional data.
“The best mobile forensic software, such as: UFED (Cellebrite), Oxygen Forensic, XRY (Microsystemation), Secure View (Susteen), MOBILedit Forensic can extract data from Android devices by installing an agent program on the device.”
As noted by Reiber (2019:57) MobileEdit Forensics, scans the connected device and if an Android device is detected, it uploads an agent program Forensic Connector and using this agent, it extracts data from the device.
“An example ... would be using a software tool on an Android device with an Android application package (APK) file... The APK queries the Android device’s internal databases and returns the data to the software interface. The data is then displayed in the software’s user interface. This method does not return a file system, but the data that is represented by the contents of the files on the device.”
Logical extraction is not guaranteed for all devices, even if unlocked. Cellebrite’s Product Updates for example lists supported phones.
Using vulnerabilities
As with all forms of extraction, there are several components which will influence whether it is possible. First is the operating system. If it’s Android, if USB debugging has been enabled, which enables the ADB server on the device and the RSA keys (security prompt) has been accepted and the personal computer (“PC”) and phone paired, then a logical extraction can be performed. As noted, this is typically an ADB backup combined with pushing an Android APK to the device and using available commands to extract active records like SMS/MMS, Call Logs and Contacts.
Mikhaylov (2017:39) states that different steps are required to activate USB debugging mode depending on what version of Android is being used. To enable USB debugging the passcode will be required. Although some devices running Android, like the Innotab Max, which Privacy International tested in 2016-17, appear to ship from the factory with debugging enabled by default. Research by Pen Test Partners confirmed that the Vtech Innotab Max is rooted by default with ADB (auto debugging) enabled from the outset.
USB debugging mode is a developer mode in Android phones that allows newly programmed apps to be copied via USB to the device for testing. It allows an Android device to receive commands, files and the like from a computer and allows the computer to pull crucial information like log files from the Android device. Enabling USB debugging leaves the device exposed. The ADB, Android Debug Bridge is a command-line utility included with Google’s Android SDK. ADB can control your device over USB from a computer.
Without USB debugging logical extraction is unlikely to be possible, unless a vulnerability could be used. A logical extraction may be available depending on factors such as phone type, vulnerability used, software version and so on. Another way of looking at this is to consider whether user data is stored on the internal flash memory, and if so, whether it is protected and requires root access to read.
An example of a vulnerability used for logical extraction, since it can only target a specific area of the file system is described by Christopher Vance of Magnet Forensics.
“Because this is an MTP extraction, we’re only going to be able to grab what’s in the / media / directory in the /data/ or /userdata/ partition. This is going to be mostly pictures and video files. However, the /media/ directory can hold more than that. It can also include documents, downloads from web browsers, WhatsApp chat backups, and third-party application data that developers choose to store here.”
Extracting an encrypted and damaged Samsung Galaxy S7, SM-G930V (could not enter the passcode or turn on USB debugging), using Media Transfer Protocol (“MTP”) was one option to get around passcodes and authorization. However, whilst available for some Android phones, Samsung v.6 “has changed the default connection type to “Charge Only” when it is plugged into a computer, so we would have to enable MTP which isn’t going to be possible without our [damaged] screen”. Magnet AXIOM have an ‘Advanced MTP bypass method’:
“…to grab a quick image of the / media / partition on the device for Samsung devices that have not received either the SMR-OCT-2017 or SMR-NOV-2017 security update (the exact update in which this was patched depends on the device model). Even if this device doesn’t have MTP enabled or is even locked with a passcode, this option will allow us to extract some of the data for analysis.”
Locked iPhones
Whilst“...a logical acquisition can be obtained if the iPhone is unlocked,” a locked iPhone is problematic since there are two separate prompts to deal with. One activates pairing mode with the computer and allows for an iTunes backup and one allows for media transfer if the standard iTunes provided driver cannot be found and it defaults back to MTP (Media Transfer Protocol) mode. If the device has a valid pairing record on the PC where the extraction is occurring, then a logical (iTunes style backup) can be obtained from a locked iPhone. Without that unfortunately it cannot be obtained.
In older iOS versions it was possible to gain just MTP extractions from an iPhone that was locked but this has since been patched and is the reason for the second prompt. Without accepting that prompt (hidden by the lock screen) you won’t be able to get an MTP extraction from the device.
File system extraction
What is it
File system extraction is often technically seen as a type of logical extraction. As with all forms of extraction, the capabilities of a file system extraction will be device-specific. File System Extraction is slightly more data rich than a logical extraction, in file system extraction the entire filesystem is taken off of the phone.
It “…contains much more information than the defined logical collection and should be considered a step up from a logical collection. A file system contains the files and folders that the device uses to populate applications, system configurations, and user configurations along with user storage areas.”
It includes files not directly accessible to the user via the device interface and require specialised tools to access file system artefacts. It does not extract unallocated space.
“The information contained [in a file system extraction] far exceeds any data that is collected on the surface. Collecting the “surface” logical data along with file system recovery is what every examination should strive to accomplish. This type of collection should be referred to as a file system collection, not simply a logical extraction.”
“Feature phones using proprietary file systems can have their file systems collected and displayed to show system files, user databases, media, user files, logs, user settings, and more. … These files are the actual containers queried and parsed by the logical software and displayed in the software interface. By having the actual file, you can conduct a more detailed analysis, which should be considered much more valuable than what “logical” defines.”
File System Extraction is usually done by a root user so requires (generally soft) rooting the phone. A root user is a superuser, in that a superuser has permission to do anything to any files anywhere in the phone’s system. i.e. privileged control over the phone. Rooting a phone is the process to attain root access.
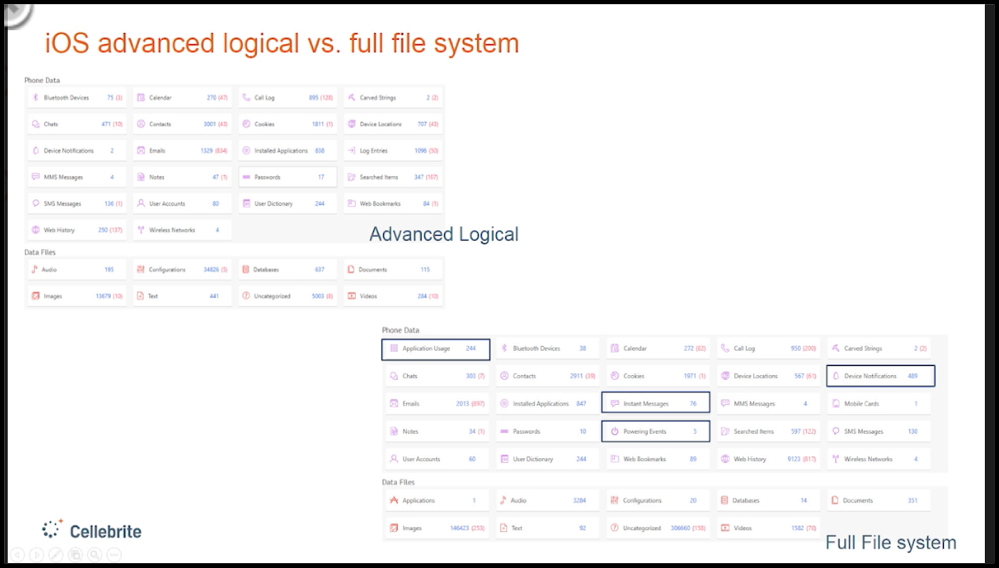
Cellebrite UFED ‘advanced logical extraction’ combines the logical and file system extractions for iOS and Android devices and is an alternative to where physical extraction is not possible.
“Advanced logical acquisitions are the same as file system acquisitions in which access to the filesystem data is provided. Physical acquisition on iOS devices using the A5-A11 chips (iPhone 4s and newer) is not possible using this tool. Thus the advanced logical acquisition method is the best support and will pull the most data from these devices if they are unlocked (even if they are not jailbroken). If the device is jailbroken, additional data can be extracted.”
How does it work?
File system extraction is less identified as a distinct form of extraction by companies. Almost uniquely Cellebrite promotes UFED’s file system extraction and is amongst the few who refer to the method:
“File system extraction with UFED Physical Analyzer is almost identical to physical extraction in that it relies on a boot loader to access the device’s memory; however, rather than obtain a bit-for-bit image including unallocated space, the software extracts only the device file system. This extraction process is proprietary rather than dependent on Apple’s API.”
MSAB does not have a specific file system product, simply XRY Logical and XRY Physical. Oxygen Forensics refer to obtaining a file system collection as part of ‘classic logical’. Magnet’s Acquire tool allows you to choose an extraction process, offering a ‘quick extraction’ from all iOS and Android devices or ‘full extraction through a physical image of rooted Android devices or file system logical images of jailbroken iOS devices.'
“If the device is rooted you can create a physical dump. If the device is not rooted a backup of the device is created and all the files that are in the memory card of the device are extracted.”
File system acquisition is however an alternative where physical extraction of iOS devices is no longer possible. Unfortunately, the passcode is required.
“Since iOS 8, removing the passcode is pointless even on 32-bit devices. The cryptographic key that’s needed to decrypt the data partition is calculated dynamically based on user input (the passcode) and keys from Secure Enclave. Without the correct passcode, the iPhone will remain encrypted; there’s simply no way around it.”
Secure Enclave “is a hardware-based key manager that’s isolated from the main processor to provide an extra layer of security.” The consequence is that encryption keys are protected by Secure Enclave and are no longer accessible even if the device is jailbroken. However, a file system extraction can be obtained if you jailbreak the device. To do this you need to boot and unlock the device using the passcode. “In other words, the passcode must be known in order to perform the (limited) physical acquisition of all iPhone devices starting with iPhone 5s.”
“Secure Enclave has brought new challenges to iOS forensic examiners. Now, we can’t extract encryption keys required to decrypt the device image, so physical acquisition is useless. But here comes the filesystem acquisition. Unfortunately, it requires the iOS device to be jailbroken.”
Unlike a logical extraction, once the file system has been obtained it will need to be decoded.
“The decoding process translates the raw data within a database file to a recognizable format. Data extracted via APIs and backups require no decoding because it is intrinsic to these methods, which present media files such as pictures and videos as they are seen on the device. However, data within other database files, such as those that contain text messages, must be separately decoded to parse out the messages. UFED Physical Analyzer automatically performs this decoding process, presenting decoded data both in human-readable format, and as raw data is stored in the device’s memory.”
Using vulnerabilities
Cellebrite claims its full file system extraction of an iOS device using their in-house labs ‘Cellebrite Advanced Services’, can obtain 21GB from a 32GB Flash Memory. Cellebrite promotes its ‘Advances Services’ instead of releasing valuable vulnerabilities into the UFED, as this will, for example, give Apple a chance to patch exploits. Thus, what vulnerabilities are used to carry out a full file system extraction of an iOS device are not publicly disclosed.
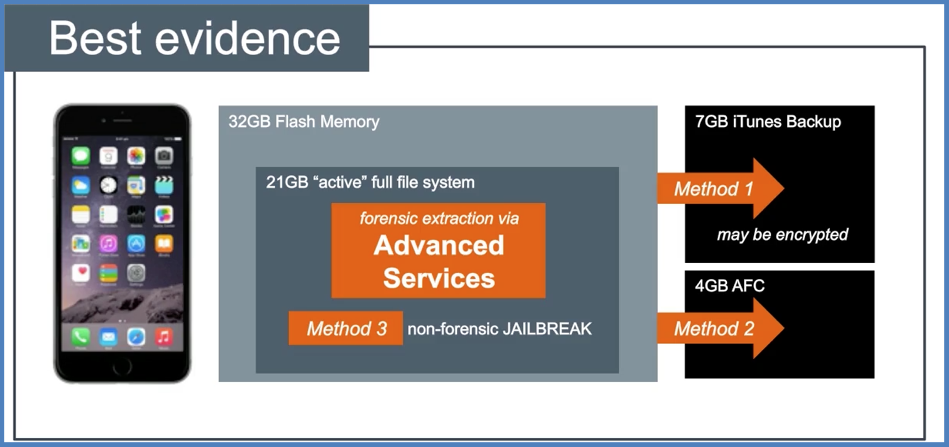
“What is the benefit of performing a full file system extraction instead of logical, file system or even an advanced logical extraction? There are three main benefits. Getting data from third party apps is the first one. WhatsApp, Facebook messenger, telegram. The data cannot be recovered unless a full file system extraction is performed. These apps and many more can hold critical information which can help close your case.”
I.e. A full file system extraction can obtain third party apps excluded from an iTunes backup. It can also identify device locations of interest, reveal system logs and application log data.
The use of Cellebrite Advanced Services has not been without controversy. In June it was reported that UK digital evidence lab Sytech lost its accreditation after a former employee reported concerns about the handling of evidence at the business. This included phones being ‘sent abroad to be decrypted without the knowledge of the police’. One former employee said that ‘a police force, understood to be Greater Manchester police, raised concerns with Sytech last year after learning that phones had been sent abroad to be unlocked by the Israeli-founded, Japanese owned company Cellebrite.’
Magnet Forensics also states that it can obtain a full file system. It has partnered with GrayKey to offer “the most advanced solution to recover data from an iOS device including the full file system, decrypted keychain and process memory whereas other tools are limited to an iTunes backup only.” GrayKey can reportedly unlock iOS devices and get around USB Restricted mode.
Magnet Forensics report that they can then get third-party application data unlike an iTunes backup, aspects of Apple Mail data, web cache and app cache, operating system data, location data, keychain data and some deleted messages:
“GrayKey can obtain a full-file system image of the device which means that temporary or support files that exist with our standard artifacts are now available for review. A prime example of this is the sms.db-wal file that lives in the same directory as the sms.db. The sms.db allows examiners to recover and parse iMessages, SMS messages, and MMS messages. However, because this database utilizes the “write ahead log” functionality of SQLite, messages are in fact written to the sms.db-wal file before being committed into the main sms.db. This can cause issues in recovering potentially deleted messages depending upon how long the messages were on the device before being deleted. If messages are deleted as soon as they are sent/received it’s much less likely to be able to recover these messages from a standard iTunes style extraction. However, since GrayKey allows us to extract the full file system, we now have access to this file and AXIOM will attempt to carve for any traces of messages left behind in the write ahead log including potentially deleted messages.”
There is little information around file system extraction, perhaps given the value of iPhone vulnerabilities. There is also not much about other operating systems such as Android, perhaps because it is still possible to carry out the preferred physical extraction.
Physical extraction
What is it?
Physical extraction can obtain “service data, applications, and user’s data. Deleted files can be restored from the physical dump.” Physical extraction is a bit-by-bit copy of the physical storage / entire filesystem / device memory or as a hex-dump. It usually requires specific cabling, and involves booting the phone into a custom OS, or recovery. Physical Extraction generally takes a long time, because it brings over free space too, however freespace can contain deleted information so may be worthwhile from an investigators point of view.
“Physical extraction has long been an ideal forensic extraction method for cell phones and embedded devices. This method has traditionally included physical access to the memory chip to obtain a raw reading of the underlying flash blocks. Not only does this method allow access to the digital data, but analyzing the physical storage quickly reveals unused areas and blocks that can contain deleted data and hold significant forensic value.”
It is the most comprehensive and invasive of all the extractions and includes all unallocated space on the phone which is why it may include deleted files.
“Cellebrite’s physical extraction capability accesses the additional data layers, in both allocated and unallocated space, that construct the phone’s physical memory. These layers include three different groups of content pertinent to investigators:
“Logical” content unavailable through API (e.g. call logs on smartphones and feature phones)
Deleted content
Content that the phone collects without any user action (and sometimes without user knowledge). For example: wi-fi networks, GPS locations, web history, email headers and EXIF data on images and system data.”
How does it work
“A hex dump, also referred to as a physical extraction, is achieved by connecting the device to the forensic workstation and pushing unsigned code or a bootloader into the phone and instructing the phone to dump memory from the phone to the computer. Since the resulting raw image is in binary format, technical expertise is required to analyze it. The process ... provides more data to the examiner, and allows the recover of deleted files from the device-unallocated space on most devices.”
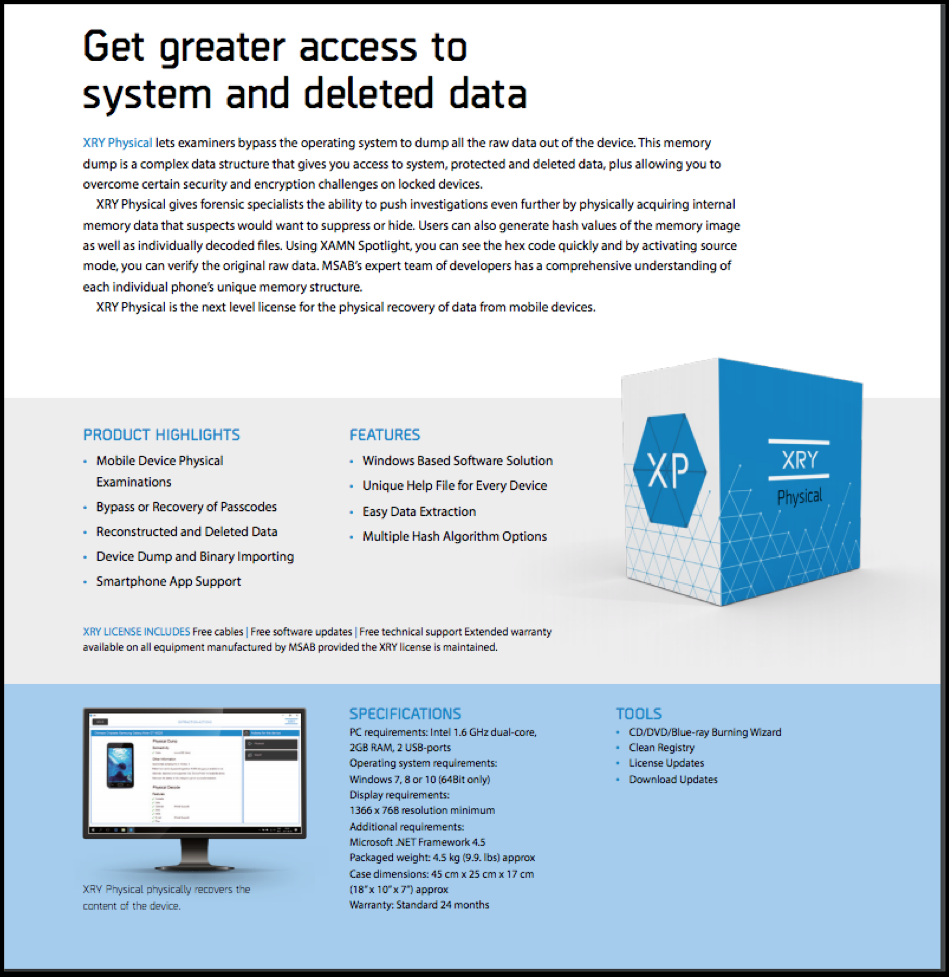
MSAB state that their XRY Physical product accesses the data through bypassing the operating system to access all system and deleted data. They can overcome security and encryption challenges on (certain) locked devices.
“The physical collection of a mobile device’s data should imply that direct communication with a device’s internal data storage is made to collect a representation of the data as it is stored on the actual device flash memory. This data is a snapshot in the area of the flash memory store that is accessible using specialized tools and methods.”
“...with encryption enabled on the full disk, at the block-level, entire physical reading becomes unusable unless an examiner can retrieve a device’s encryption key.”
The XRY Physical add-on to XRY Logical enables the user to conduct password bypass of some Android devices, on-board memory chip reads, and other advanced mobile forensic tasks.”
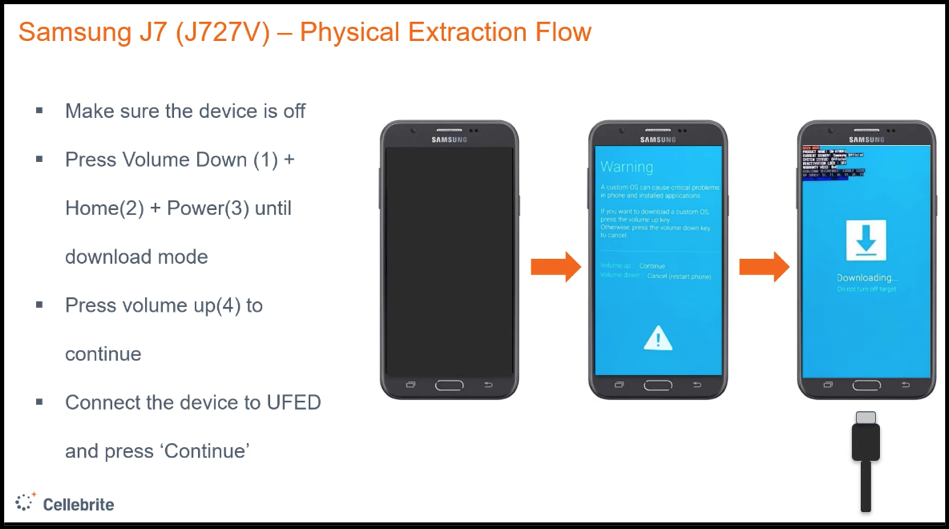
On an Android phone, this method usually requires the removal of the battery and the turning off of the phone, also the cable is usually specific for this method, rather than using the standard charging cable. The Cellebrite directs throughout what steps must be undertaken and when, including which buttons need to be held at startup to enable FastBoot, Bootloader, Recovery, Factory Reset etc, depending on which devices are being extracted.
Once the device is in fastboot, the Cellebrite works fairly automatedly, it may prompt you at times to select options on the phone screen or restart the phone.
The physical extraction, which we did on a iPhone 4, uses a bug in the iOS bootstrap process which allows for unsigned code to executed (its a technique used to jailbreak older iDevices) the Cellebrite then runs its own OS instead of iOS and extracts the data from the phone.
Physical extraction might use a phone’s rescue mode or download mode. “Operating in this mode, mobile phones are designed to allow the insertion of a small piece of code, called bootloaders, into the RAM during start-up.” The bootloader will read the contents of the device’s memory and send it back to extraction device. Cellebrite states that:
“… During the initial stage of the device’s booting, the UFED sends the boot loader to the device’s RAM memory. The device will start running the boot loader, but will not continue its regular booting procedure into the OS. The Cellebrite boot loaders then execute “read only” actions that extract evidence from mobile devices and leave no artifacts behind.”
Cellebrite’s bootloaders are designed in-house around each individual device platform taking into account the varieties in chipsets, peripherals, memory chip interfaces and USB controllers. Customers will need to send certain phones to Cellebrite.
“UFED has obtained the permission to access operating system internals after the data is already decrypted. It can then extract the raw, block-level reading in decrypted form. This is done, again, by exploiting vulnerabilities identified by Cellebrite. These vulnerabilities are rarely available to the public after they are discovered. Quite often, Cellebrite’s Security Research Labs have exclusive knowledge of vulnerabilities and the opportunities they afford.
This knowledge will only become more valuable; as iOS & Android software progresses and privacy protections, sandbox isolation mechanisms and security mitigations advance.”
The iOS challenge
Apple’s iOS presents the biggest hurdle for physical extractions. Before the iPhone 4S you could carry out a physical extraction on an iPhone. But since iPhone 4S and indeed for other devices that have entered the market, it is extremely difficult if not impossible to get into the device due to hardware encryption. Although a number of vendors’ state they can.
“Physical acquisition has the greatest potential for recovering data from iOS devices; however, current and evolving security features (secure boot chain, storage encryption, and passcode) on these devices may hinder the accessibility of the data during forensic acquisition. Researchers and commercial forensic tool vendors are continually attempting new techniques to bypass the security features and perform physical acquisition on iOS devices, but for the latest model the only available option is jailbreaking and even this won’t help you to physically acquire devices with Secure Enclave…”
Elcomsoft iOS Forensic Toolkit 5.0 states that it can achieve iOS 12 physical extraction. This sounds similar to Cellebrite’s full file system extraction described above. It can extract the content of the file system and decrypt passwords and authentication credentials stored in the iOS keychain. It is possible on devices supported by the ‘rootless jailbreak’.
“Elcomsoft iOS Forensic Toolkit supports all possible options for extracting and decrypting data from both jailbroken and non-jailbroken 64-bit devices, including the last generations of Apple hardware and software. Without a jailbreak, experts can perform logical extraction though iOS system backups, extract shared app data and media files. In certain cases, logical extraction is even possible if the iPhone is locked. If a jailbreak can be installed, experts can image the file system of 64-bit iPhones, extract protected application data and working datasets.”
“Physical acquisition offers numerous benefits compared to all other acquisition options by enabling access to protected parts of the file system and extracting data that is not synced with iCloud or included in local backups: In particular, physical acquisition is the only method for decrypting keychain items targeting the highest protection class. File system extraction gains full access to application sandboxes and all system areas, extract secret chats and recover deleted messages. Downloaded email messages, chat databases and secrets from two-factor authentication apps, system logs and detailed location data are just a few things that are exclusively available with file system extraction.”
“...public jail breaks to gain access to the device’s file system, circumvent iOS security measures and access device secrets allowing us to decrypt the entire content of the keychain including keychain items protected with the highest protection class.”
Indeed, Reiber (2019 : 342) states that:
“With today’s iOS devices containing A5 and later chipsets, a non-jailbroken physical bit-by-bit collection using a USB is impossible, so a logical file system collection is the only available method…Some sources report that a physical collection can be obtained using tools such as Elcomsoft iOS Forensic Toolkit, GrayKey by Grayshift, or Cellebrite’s professional services CAIS program, but this is not entirely accurate. These tools cannot be used to perform a physical partition collection as they can with A4 chipsets; they simply enable collecting a jailbroken device’s internal file system. Once the device is in a state in which a raw file system can be collected, most commercial tools, including UFED Touch 2, Oxygen Forensic Detective, and XRY, can collect the file system and artifacts.”
Physical acquisition of iOS 11 devices by Elcomsoft iOS Forensics Toolkit uses classic jailbreak.
“Forensic experts use jailbreaks for much different reasons compared to enthusiastic users. A wide-open security vulnerability is exactly what they want to expose the device’s file system, circumvent iOS sandbox protection and access protected data. Jailbreaking extracts the largest set of data from the device. During jailbreaking, many software restrictions imposed by iOS are removed through the use of software exploits.
In addition to sandboxed app data (which includes conversation histories and downloaded mail) experts can also extract and decrypt the keychain, a system - wide storage for online passwords, authentication tokens and encryption keys. Unlike keychain items obtained from a password-protected local backup, physical extraction of a jailbroken device gains access to keychain items secured with the highest protection class.”
Android - Using vulnerabilities: Emergency Download Mode
“It may seem unusual, but it is possible to make a physical dump of an Android device without rooting and it does not require JTAG and Chip-off methods.”
Emergency Download (EDL) mode is a vulnerability used by a number of vendors to carry out physical extractions. It works on some but not all devices that have the Qualcomm chipset. EDL is Qualcomm’s rescue mode for phone diagnostics and repair, which is exposed through various triggers or when a device cannot boot. It “is designed to allow low level access to chipset for device analysis, repair or re-thrashing.”
Cellebrite has a wide range of ready ‘programmers’ which are “pieces of software containing raw flash read/write functionality”. Programmers can be digitally signed with a vendor signature that is verified by the device, so for EDL to accept and verify a programmer it must match but the hardware and signature requirement.
When Cellebrite’s UFED starts EDL extraction flow, it will automatically attempt to match an existing programmer it has to the hardware and signature requirement. If there is a match, then it will have flash read access. If there is not signature requirement for a particular phone, then it will match the hardware. According to Cellebrite, UFED has a proprietary exploit to bypass the signature requirement for several chipsets.
In addition, raw flash access will enable access to encrypted content, however, without access to encryption keys. To address this problem, Cellebrite UFED will attempt to fully boot the device before the extraction begins.
The way you put a device in EDL mode will differ depending on the phone and ranges from techniques that various technologies such as Cellebrite’s UFED can support, to more invasive techniques that require forensic skill. If EDL is supported by Cellebrite, the UFED can guide you through what you need to do, for example, hold vol up and down.
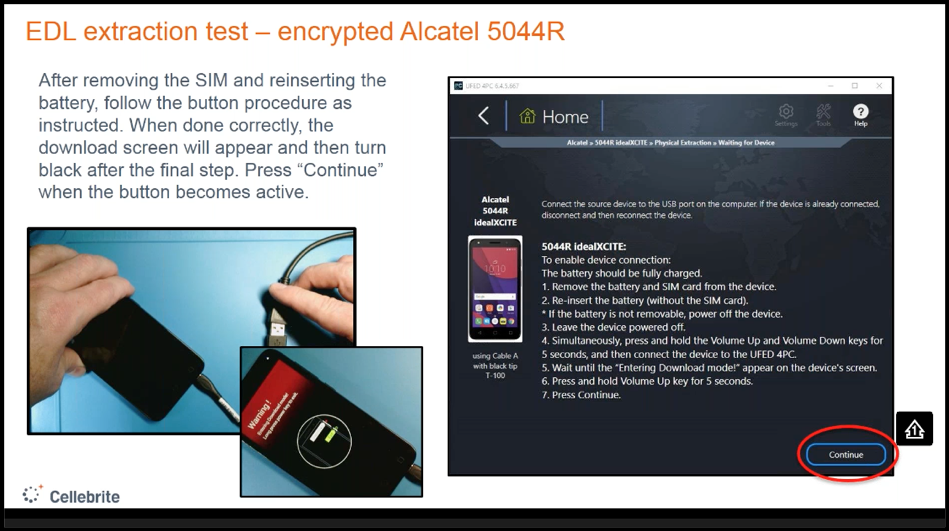
Cellebrite’s UFED has both a decrypting and non-decrypting EDL extraction option. Both work on pattern or passcode locked devices (if the device is supported), if the device is encrypted. The decryption extraction for encrypted devices will require the device to boot so that the UFED can apply the decrypting bootloader, which is not required for non-decrypting EDL extraction. For both options, when using the UFED, the user will be able to choose placing the device in DFU (handset diagnostic interface) FTM (factory test mode). These both use EDL methods.
An example of using EDL mode, bootloader option is Cellebrite’s EDL physical bypass solution for certain Samsung devices with the Qualcomm chipset. Most modern phones running Android are encrypted out of the box. In this method Cellebrite uses specified cables for devices with a specific data port connection. When the device is running in bootloader mode, the operating system does not run. It bypasses any user lock. When you select the phone you want to download, the UFED will ask you to do a number of things to get the phone into download mode and enable the extraction.
Other methods to achieve EDL mode include the use of cable 523, ‘abd reboot edl’, ‘fastboot oem edl’, test point and eMMC fault injection (shorting). The last two require experience with ISP and Chip Off.
Cellebrite are not the only vendor extracting a physical image for devices with Qualcomm chipsets via EDL mode. Magnet Forensics and Oxygen Forensics do this using the ADB method. Both note that ADB access has to be enabled. To do this the phone must be unlocked and USB debugging turned on “so that you’re able to send and received ADB commands to the phone … the method does work quite well in scenarios where the phone is already unlocked and you just want to get a better acquisition.” Oxygen Forensics also use ‘fastboot’ and describe getting devices into this mode using key combinations e.g. holding Power and Vol- at the same time.
Cellebrite also promotes its ability to use ‘smart’ ADB:
“With this ground-breaking capability, Cellebrite restores physical extraction access to many new devices with Full-Disk Encryption enabled, when ADB can be enabled. The method requires Android 6 and above and has a wide generic coverage for many vendors.”
Oxygen Forensic Detective states that use of EDL mode “allows investigators to utilize this non-invasive physical acquisition technique and screen lock bypass on more than 400 unique devices when the phone can be successfully placed into EDL mode.”
Analysis: Analytics on extracted data
A number of tools with impressive analytical capabilities are on offer to help investigators deal with extracted data.
“There are a lot of tools for analysis of physical dumps and backups of mobile devices running Android operating systems. These tools include all the best mobile forensics tools, such as UFED Physical Analyzer (Cellebrite), Oxygen Forensics (Oxygen Forensics, Inc), XRY (MSAB), MOBILedit Forensic Express (COMPELSON Labs), and Secure View (Susteen).”
“Examination and analysis using third-party tools is generally performed by importing the device’s memory dump into a mobile forensics tool which will automatically retrieve the results.”
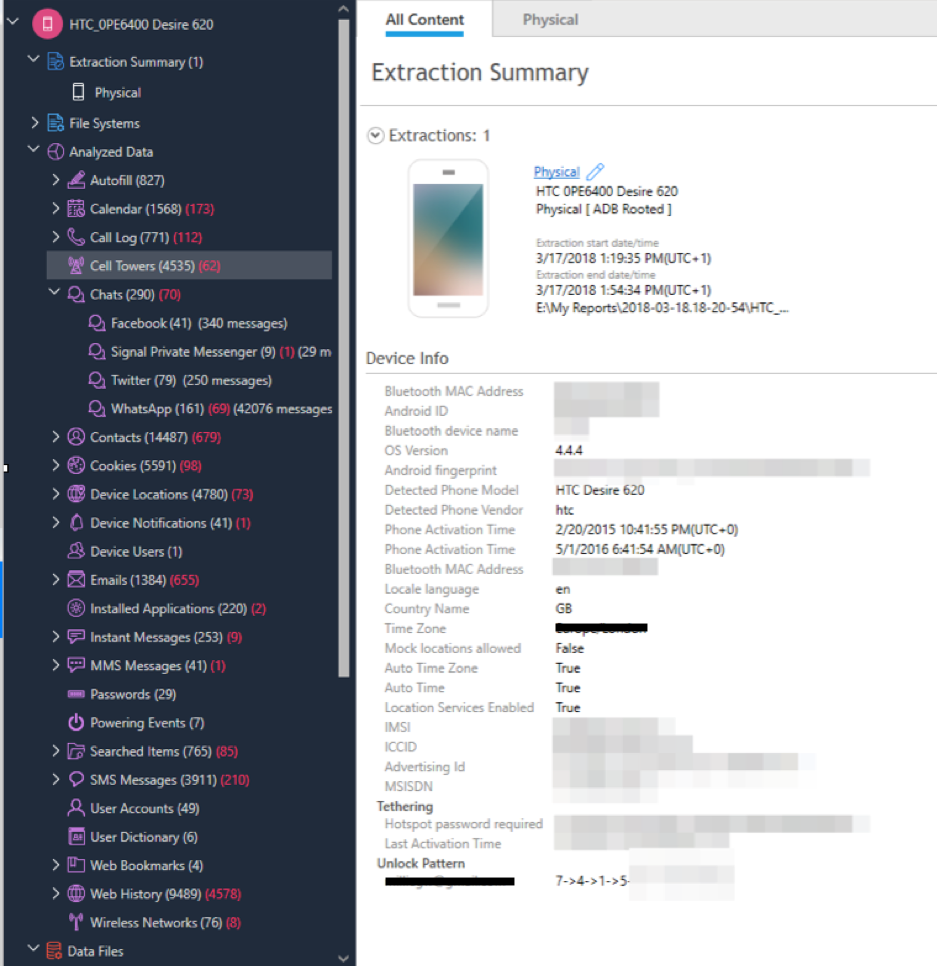
Cellebrite’s Physical Analyzer is a user-friendly piece of software that is designed to organise data extracted in different file types from XML, CSV, TXT to CDR, media and text. It can bring together datasets from different devices, recognise and categorise digital media. Physical Analyzer can display all the information that was extracted. It also has considerable data diving and visualisation capabilities.
“The analytics system unifies all drone, mobile, cloud, computer and telecommunications data in a centralised view so you don’t waste previous time using separate tools.”
Link analysis is used to analyze phone calls, emails text messages and location data in order to discover associations between individuals via different types of data. As noted by Professor Peter Sommer in evidence to the UK Parliament:
“Use is also made of data visualisation / link analysis techniques to demonstrate frequencies over time of contacts between phone numbers and between IP addresses, financial transactions and chronologies of events among others.”
Police in the UK are trialling Cellebrite’s machine learning tools to interpret images, match faces and analyse patterns of communication. Cellebrite states that:
“... data can be extracted along with other sources of critical information, such as online activity from email and social media accounts. These sources can then be filtered, compared and analysed using artificial intelligence and machine learning to generate actionable insights, such as locations…Extracted data can be combined with data from public sources - such as websites or social media accounts - to find crucial information and make comparisons. Investigators can use the combined data to build profiles of attackers, their contacts, and members of wider terror cells. The data can also create timelines of events, helping investigators to determine exactly what has happened and compile the right evidence for a prosecution.”
Magnet AXIOM is also utilising machine learning techniques:
“...with features like Connections and Magnet.AI, you can automatically generate insights that could lead to important breakthroughs in your examinations.
“Machine learning, via Magnet.AI, offers … a predictive apparatus “trained” to recognize messages that fall into … categories.”
“With the launch of AXIOM 2.0, the Magnet.AI module now identifies images that may contain depictions of child sexual abuse, nudity, weapons and drugs. We’ve also expanded our text classification model to detect potential sexual conversations in addition to child luring.”
In August 2017 Cellebrite introduced what it called “advanced machine learning technology” for its analytics platform, which can be used to analyse data extracted from the cloud and which included face recognition and matching.
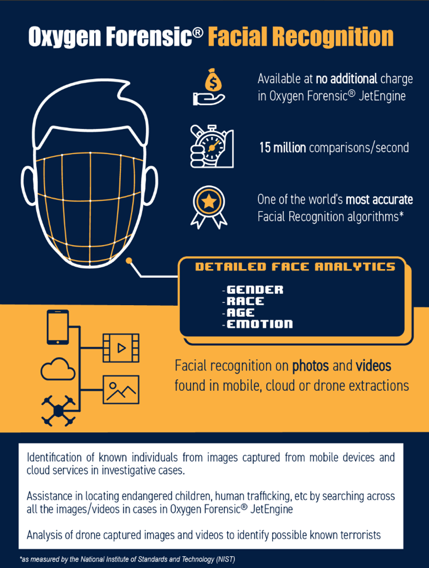
From July 2019, Oxygen Forensics JetEngine module, built into Oxygen Forensic Detective, provides the ability to categorise human faces using their own technology. Not only do they provide the categorisation and matching of faces within extract data, facial analytics is included gender, race and emotion recognition. Lee Reiber, Oxygen’s chief operating officer said the tool can “search for a specific face in an evidence trove, or cluster images of the same person together. They can also filter faces by race or age group, and emotions such as “joy” and “anger”.”
Conclusion
As the use of mobile phone extraction proliferates, whether it is used by law enforcement or border security, the data from these devices will be used to challenge an individual whether in criminal, civil or immigration proceedings and procedures. There is little technical information available to individuals, to those who may represent them and those who campaign on these issues. Whilst mobile forensics is a rapidly changing field, this is an attempt to look at what is going on when those who use powerful extraction tools seek data from devices.
The use of mobile forensics raises issues complex issues relating to the reliability of the extracted data as a form of evidence, particularly if it is used by unskilled individuals who rely on the push button technologies but are not digital forensic analysts.
“What I am seeing in the field is that regular police officers are trying to be digital forensic analysts because they are being given these rather whizzy magic tools that do everything, and a regular police officer, as good as he may be, is not a digital forensic analyst. They are pushing some buttons, getting some output and, quite frequently, it is being looked over by the officer in charge of the case, who has no more training in this, and probably less, than him. They will jump to conclusions about what that means because they are being pressured to do so, and they do not have the resources or the training to be able to make the right inferences from those results. That is going smack in front of the court.”
The delivery of justice depends on the integrity and accuracy of evidence and trust that society has in it. We hope that in starting to unpick some of the complexities in this field, we can inform the debate on this topic.



