Search
Content type: Long Read
Photo by Nadine Shaabana on Unsplash
Digital identity providers
Around the world, we are seeing the growth of digital IDs, and companies looking to offer ways for people to prove their identity online and off. The UK is no exception; indeed, the trade body for the UK tech industry is calling for the development of a “digital identity ecosystem”, with private companies providing a key role. Having a role for private companies in this sector is not necessarily a problem: after all, …
Content type: News & Analysis
The latest news of Twitter “inadvertently” sharing email addresses or phone numbers provided for safety or security purposes (for example, two-factor authentication) for advertising purposes is extremely concerning for several reasons.
First of all, it is not the first time for Twitter's used people's data in ways they wouldn't expect or that ignores their choices: in August, the company disclosed that it may have shared data on users with advertising partners, even if they had opted out from…
Content type: News & Analysis
Photo by Daniel Jensen on Unsplash
Everyone is talking about Facebook's end-to-end encryption plans and the US, UK and Australian government's response. Feeling lost? Here is what you need to know.
What's Facebook trying to do?
First let's be clear: Facebook has many faults when it comes to privacy. It's also suffered a number of security failures recently. See here for instance.
In response to their successive failures to protect your privacy, Facebook announced in their 'pivot to privacy…
Content type: News & Analysis
Today’s announcement regarding the UK and US agreement signed pursuant to the US CLOUD Act is being touted on both sides of the Atlantic as a major victory for law enforcement and security. But it is a step backward for privacy.
And it’s far more complicated than their press release and letter to industry.
The agreement replaces the prior system, under which law enforcement agencies from around the world, including the UK, had to meet US legal standards in order to get access to content held…
Content type: Long Read
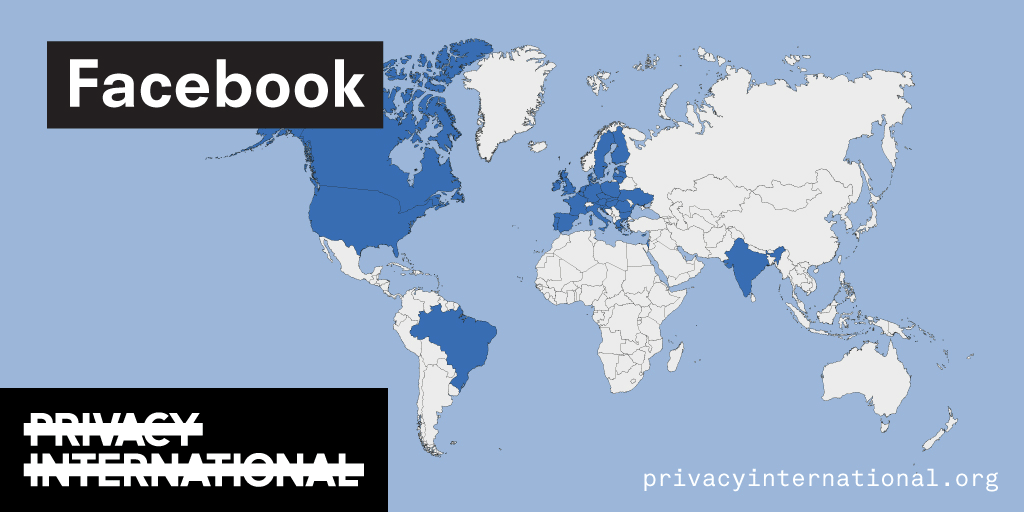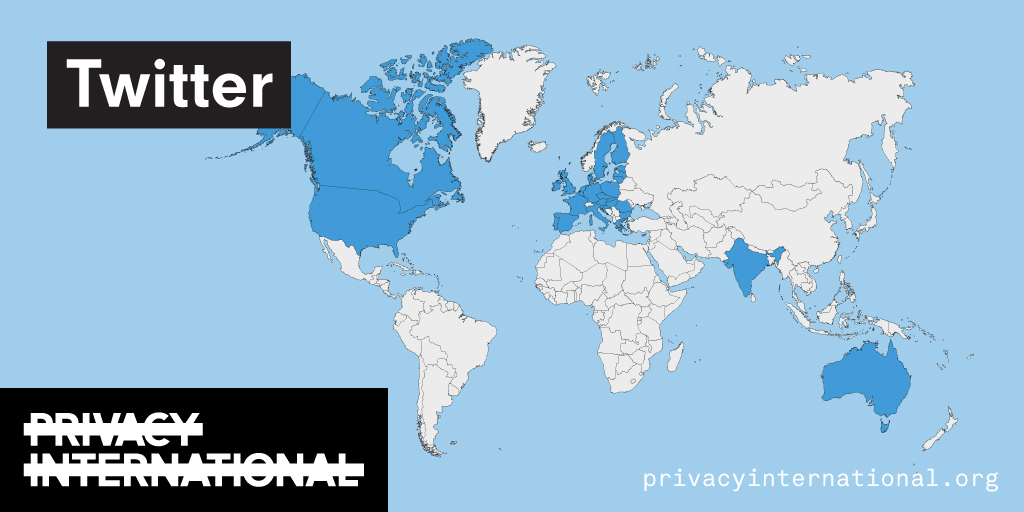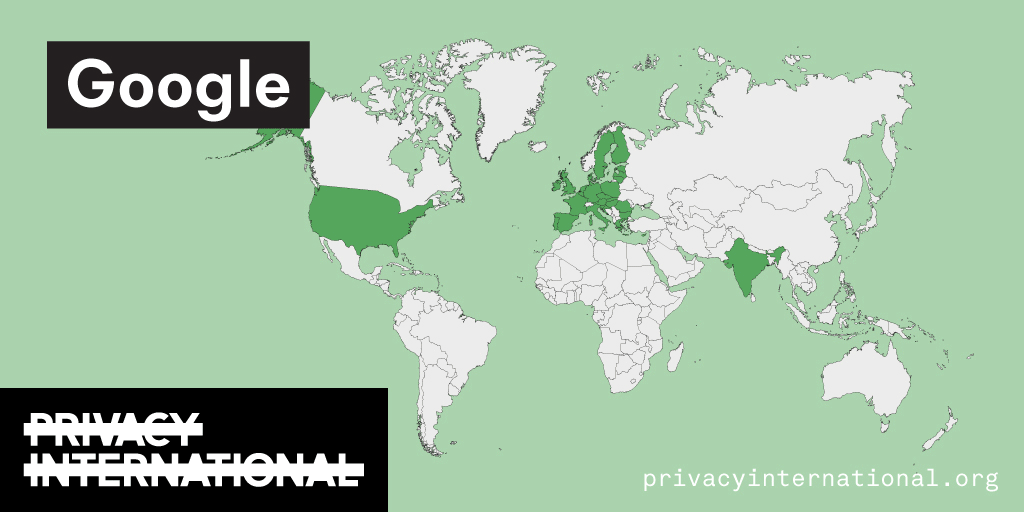
An analysis of what Facebook, Google, and Twitter have done to provide users with political ad transparency as of September 2019. Our full analysis is linked below.
Recently the role of social media and search platforms in political campaigning and elections has come under scrutiny. Concerns range from the spread of disinformation, to profiling of users without their knowledge, to micro-targeting of users with tailored messages, to interference by foreign entities, and more. Significant…
Content type: Examples
Rewire.News has reported that Google apparently remains unwilling to differentiate its Maps search results between clinics in the US that offer abortion care and faith-based organisations that do not provide abortion care.
Rewire.News reports that, in contrast Yelp "made a concerted effort" to ensure that the company differentiated between faith-based centres, also known as crisis pregnancy centres in the US, and medical facilities that provided medical reproductive healthcare, including…
Content type: Advocacy
We welcome the effort by the Government of Kenya to give life to and specify the right to privacy, already enshrined in Article 31(c) and (d) of the Constitution of Kenya by proposing a draft Data Protection Act. We particularly appreciate the direct reference to this Constitutional right in the purpose of the Act and the way it is referred to on several occasions in this proposed Bill.
Development of an effective and comprehensive Data Protection law in Kenya is a priority. In…
Content type: News & Analysis
A new UK Times report claims that “WhatsApp, Facebook and other social media platforms will be forced to disclose encrypted messages from suspected terrorists, paedophiles and other serious criminals under a new treaty between the UK and the US.”
Several other media outlets have followed up on the report, with headlines such as “UK and US set to sign treaty allowing UK police ‘back door’ access to WhatsApp and other ‘end to end encrypted’ messaging platforms”.
While the…
Content type: Advocacy
PI is increasingly concerned that democratic participation can be inhibited by novel and unhindered surveillance both by governments and companies. To safeguard our rights, earlier this year, we launched our work programme, Defending Democracy and Dissent, which aims to investigate the role technology plays in facilitating and/or hindering everyone's participation in civic society.
This submission to the House of Lords covers PI’s views on:
How digital tech has changed the way…
Content type: Frequently Asked Questions
Privacy is a fundamental right and shouldn’t be a luxury. But if you have a cheap phone, your data might be at risk.
Content type: Explainer
Abstract
Over the past few years, smart phones have become incredibly inexpensive, connecting millions of people to the internet for the first time. While growing connectivity is undeniably positive, some device vendors have recently come under scrutiny for harvesting user data and invasive private data collection practices.
Due to the open-source nature of the Android operating system vendors can add pre-installed apps (often called “bundled apps” or "bloatware") to mobile phones.…
Content type: Video
Christopher Weatherhead and Eva Blum-Dumontet Discuss the finding of Privacy International's report on the MyPhone MYA2 from the Philippines
Content type: App Analysis
The following is the output from Pinoy of Exodus Standalone, by Exodus Privacy
{
"application": {
"name": "Pinoy",
"libraries": [],
"handle": "com.zed.pinoy",
"version_name": "4.19",
"uaid": "D850D2DCD60B3482C1012D8DCE0382CF7D66AEB6",
"permissions": [
"android.permission.READ_PHONE_STATE",
"android.permission.INTERNET",
"android.permission.ACCESS_NETWORK_STATE",
"android.permission.WRITE_EXTERNAL_STORAGE",
"android.permission.…
Content type: App Analysis
The following is the output from MyPhone Registration of Exodus Standalone, by Exodus Privacy
{
"trackers": [],
"apk": {
"path": "/media/transfer/AndroidAnaylsis/Library/OriginalAPKs/MyPhoneRegistration.apk",
"checksum": "584fb7efe352024b52e2584de6afd6944d5bdf038c6459200c5e4a021d3f096a"
},
"application": {
"libraries": [],
"version_code": "1",
"permissions": [
"android.permission.DISABLE_KEYGUARD",
"android.permission.RECEIVE_BOOT_COMPLETED…
Content type: App Analysis
The following is the output from Facebook Lite of Exodus Standalone, by Exodus Privacy
{
"trackers": [],
"apk": {
"checksum": "8cf800fbe1626468b7af1f3b59dae657f22f0a9fb3070b80122af6171df67689",
"path": "/media/transfer/AndroidAnaylsis/Queue/com.facebook.lite.apk"
},
"application": {
"name": "Lite",
"handle": "com.facebook.lite",
"uaid": "79CC550EE0002725D1108B4580200A40D6AFA2FD",
"version_name": "49.0.0.10.69",
"version_code": "63889098",
"…
Content type: App Analysis
The following is the output from Brown Portal of Exodus Standalone, by Exodus Privacy
{
"trackers": [],
"apk": {
"path": "/media/transfer/AndroidAnaylsis/Library/OriginalAPKs/BrownPortal.apk",
"checksum": "154622e8812f2db94bf717fc4aef29a5a24569b5940e7640915cf5958acd4ad9"
},
"application": {
"name": "Brown Portal",
"version_name": "1.1.2",
"permissions": [
"android.permission.WRITE_EXTERNAL_STORAGE",
"android.permission.INTERNET",
"android.…
Content type: Advocacy
Earlier this year, the UN Special Rapporteur on freedom of expression called for an “immediate moratorium on the global sale and transfer of private surveillance technology”, warning that “unlawful surveillance continues without evident constraint”, is leading to arbitrary detention, torture and possibly to extrajudicial killings.
Without urgent action, there is every reason to believe that the situation will only get worse for people around the world.
At Privacy…
Content type: Report
In September 2019, Privacy International filed 10 access to documents requests to EU bodies regarding the transfer of surveillance capabilities to non-EU countries. The requests seek documents providing information on the transfer of personal data, surveillance technology, training, financing, and legislation to non-EU countries. The requests were submitted to:
Frontex
Europol
The European Union Agency for Law Enforcement Training
The Directorate-General for Economic and…
Content type: News & Analysis
Photo: The European Union
“Border Externalisation”, the transfer of border controls to foreign countries, has in the last few years become the main instrument through which the European Union seeks to stop migratory flows to Europe. Similar to the strategy being implemented under Trump’s administration, it relies on utilising modern technology, training, and equipping authorities in third countries to export the border far beyond its shores.
It is enabled by the adoption…
Content type: News & Analysis
Photo by Francesco Bellina
The wars on terror and migration have seen international funders sponsoring numerous border control missions across the Sahel region of Africa. Many of these rely on funds supposed to be reserved for development aid and lack vital transparency safeguards. In the first of a series, freelance journalist Giacomo Zandonini sets the scene from Niger.
Surrounded by a straw-yellow stretch of sand, the immense base of the border control mobile company of Maradi, in southern…
Content type: Long Read
Photo: Francesco Bellina
Driven by the need to never again allow organised mass murder of the type inflicted during the Second World War, the European Union has brought its citizens unprecedented levels of peace underpinned by fundamental rights and freedoms.
It plays an instrumental role in protecting people’s privacy around the world; its data protection regulation sets the bar globally, while its courts have been at the forefront of challenges to unlawful government surveillance…
Content type: Advocacy
Agreed in 2015, the EU Trust Fund for Africa uses development aid and cooperation funds to manage and deter migration to Europe. It currently funds numerous projects presenting urgent threats to privacy, including developing biometric databases, training security units in surveillance, and equipping them with surveillance equipment. There has been no decision made about the future of the Fund pending the outcome of negotiations on the EU's next budget.
This paper…
Content type: Advocacy
The Neighbourhood, Development and International Cooperation Instrument (NDICI) is a external instrument proposed under the EU's next 2021-2027 budget. It will provide funding for surveillance, border security, and migration management projects in third countries currently undertaken by a number of projects across various funds which are to form part of the NDICI. Several raise significant concerns regarding the right to privacy.
This paper summarises the NDICI and provides a…
Content type: Advocacy
This report, which was authored by Lorand Laskai, who is a JD Candidate at Yale Law School, provides an overview of the surveillance technology and training that the Chinese government supplies to countries around the world. China, European countries, Israel, the US, and Russia, are all major providers of such surveillance worldwide, as are multilateral organisations such as the European Union. Countries with the largest defence and security sectors are transferring technology and…
Content type: Advocacy
The UK government's Department for Digital, Culture, Media and Sport, along with Government Digital Services, made a Call for Evidence on Digital Identity.
In our response, Privacy International reiterated the need for a digital identity system to have a clear purpose, in this case to enable people to prove their identity online to access services. We highlighted the dangers of some forms of ID (like relying on a centralised database, unique ID numbers, or the use of biometrics). The…