Search
Content type: Long Read
(In order to click the hyperlinks in the explainer below, please download the pdf version at the bottom of the page).
Content type: News & Analysis
Planning and participating in peaceful protests against governments or non-state actors’ policies and practices requires the capacity of individuals to communicate confidentially without unlawful interference. From protests in support of LGBTI rights to protests against specific projects that undermine local communities’ wellbeing, these movements would not have been possible without the ability to exchange ideas and develop plans in private spaces.
Unlawful interference with…
Content type: Long Read
(In order to click the hyperlinks in the explainer below, please download the pdf version at the bottom of the page).
Content type: Advocacy
Privacy International's submission to the Human Rights Committee on a future General Comment on Article 21 of the International Covenant on Civil and Political Rights (ICCPR).
In this submission, Privacy International aims to provide the Committee with information on how surveillance technologies are affecting the right to peaceful assembly in new and often unregulated ways.
Based on Privacy International’s research, we provide the following observations:
the relationship between right…
Content type: State of Privacy
Introduction
Acknowledgment
The State of Surveillance in Tunisia is the result of an ongoing collaboration by Privacy International and partners.
On 14 February 2023, the United Nations High Commissioner for Human Rights voiced concern over the deepening crackdown in Tunisia targeting perceived political opponents of President Kais Saied as well as civil society.
We have updated this page to reflect important changes in the state of surveillance in Tunisia.
Key privacy facts
1.…
Content type: News & Analysis
We found this image here.
Today, a panel of competition experts, headed by Professor Jason Furman, the former chief economic adviser of in the Obama administration, confirmed that tech giants, like Facebook, Amazon, Google, Apple and Microsoft, do not face enough competition.
Significantly, the report finds that control over personal data by tech giants is one of the main causes preventing competition and ultimately innovation.
Privacy International's research has shown clear examples of…
Content type: Long Read
(In order to click the hyperlinks in the explainer below, please download the pdf version at the bottom of the page).
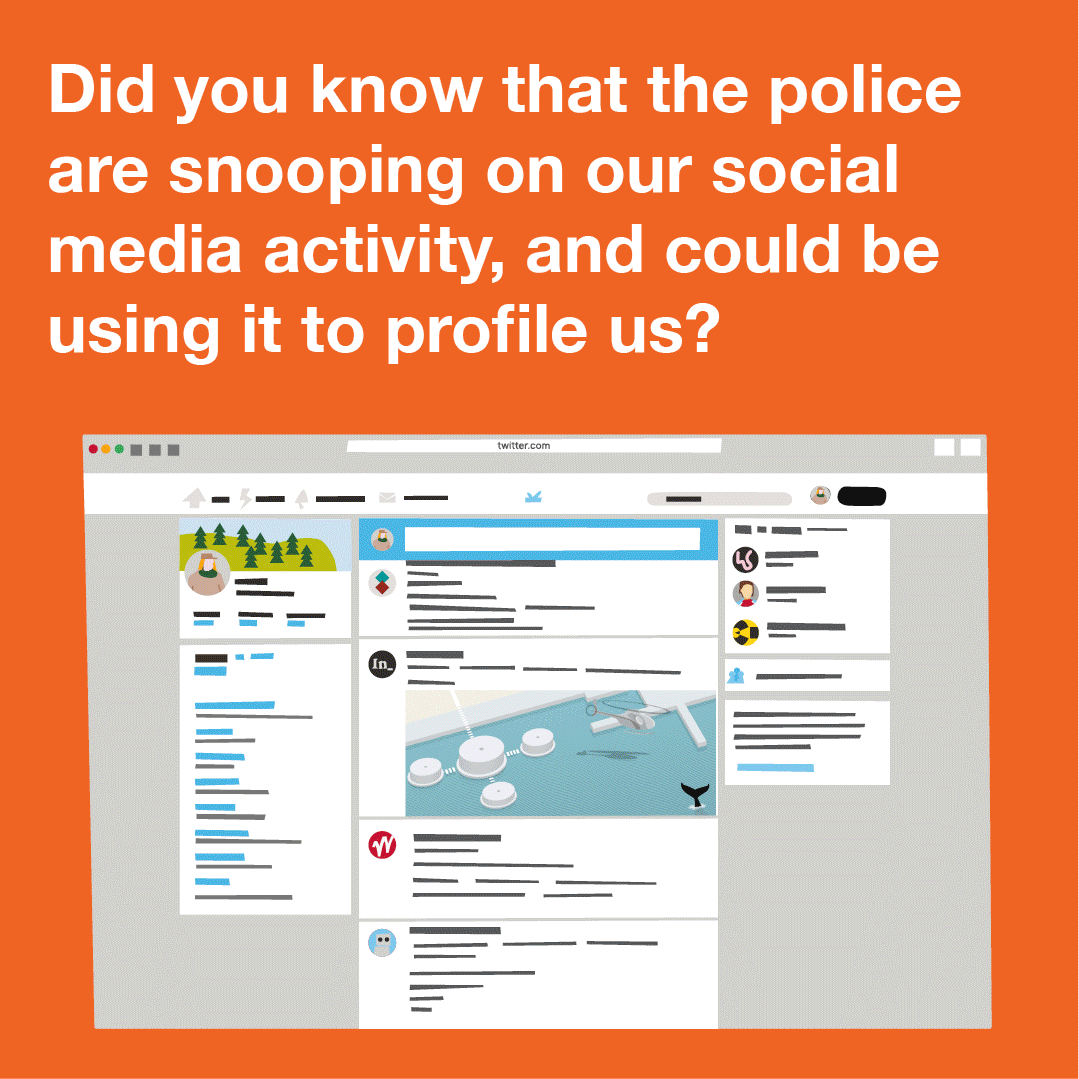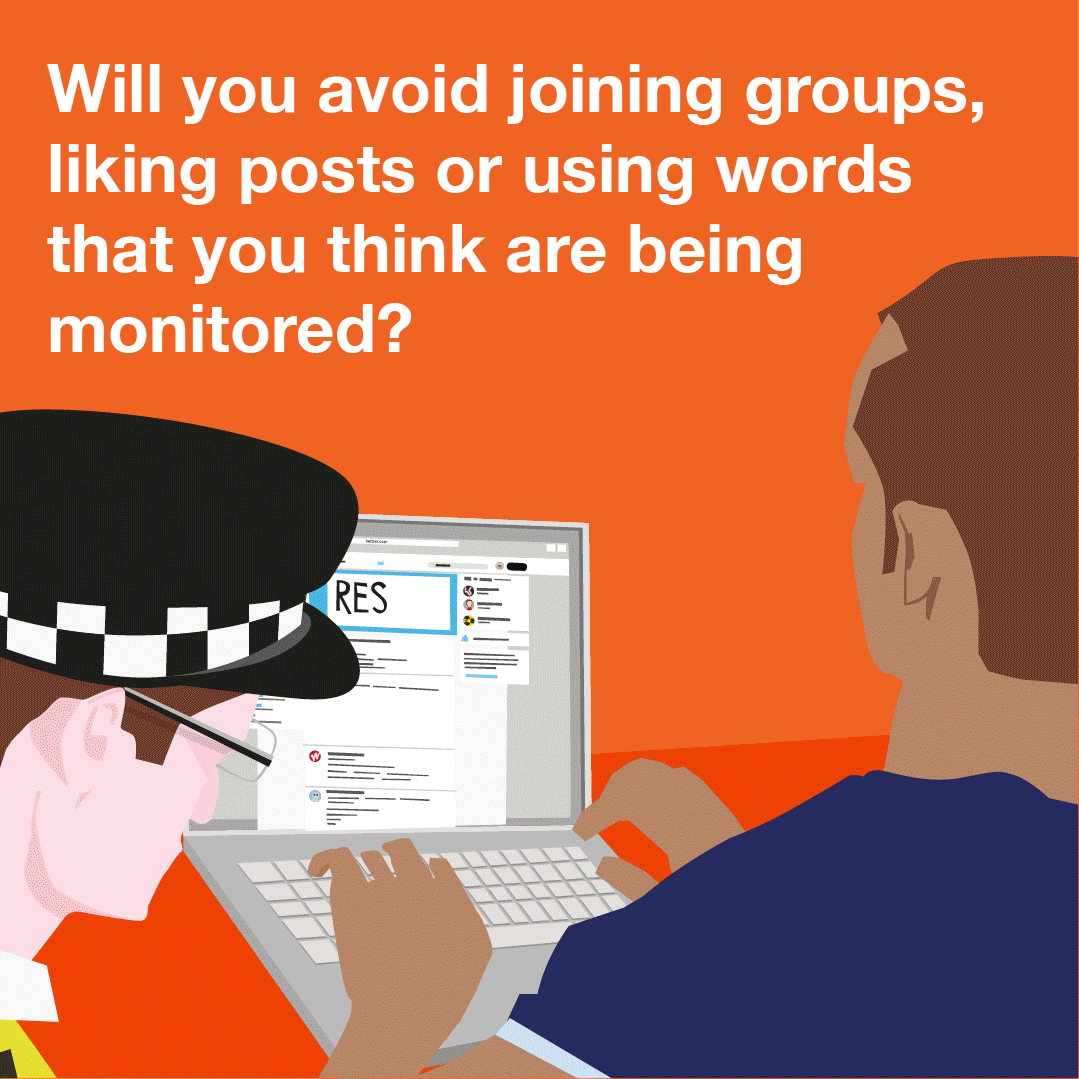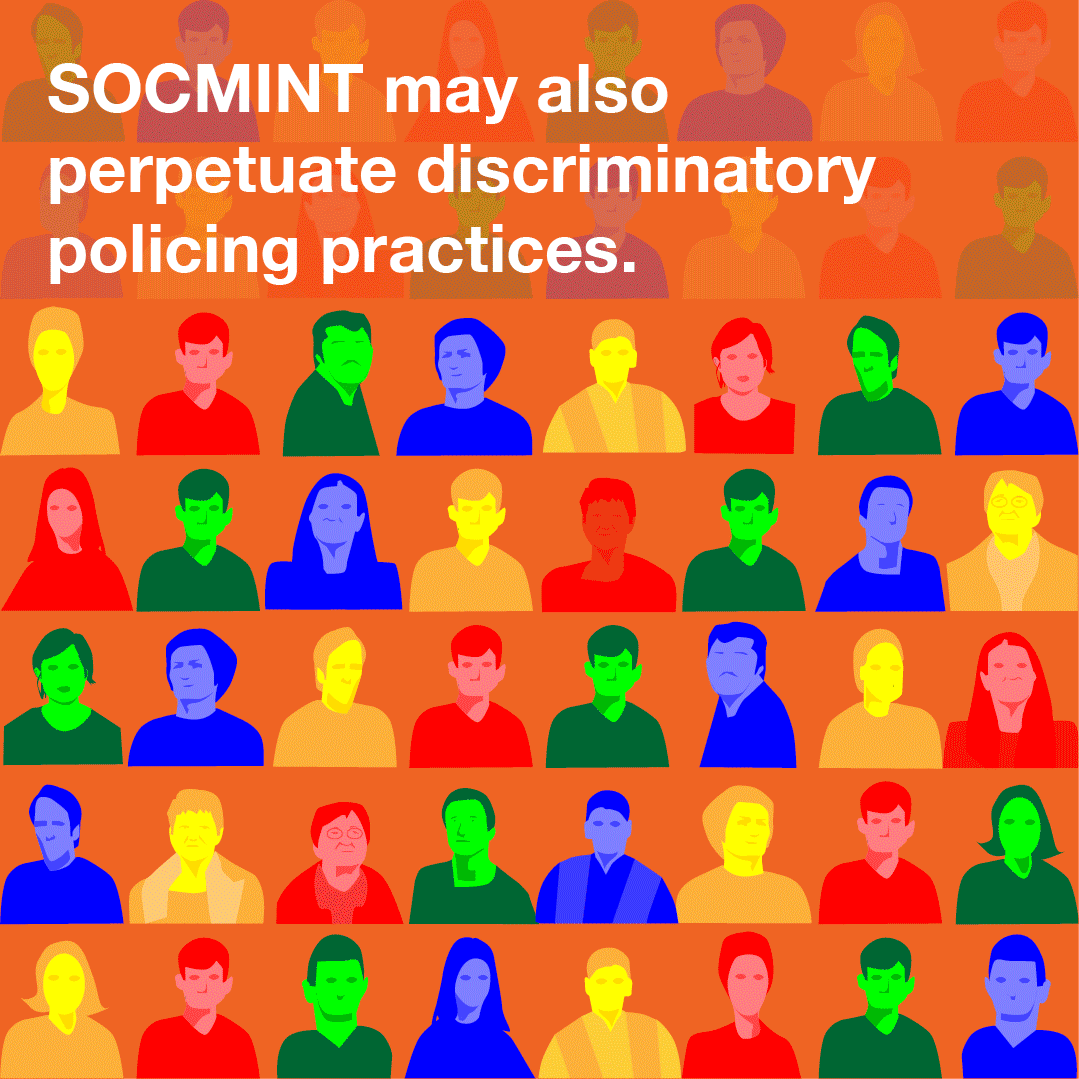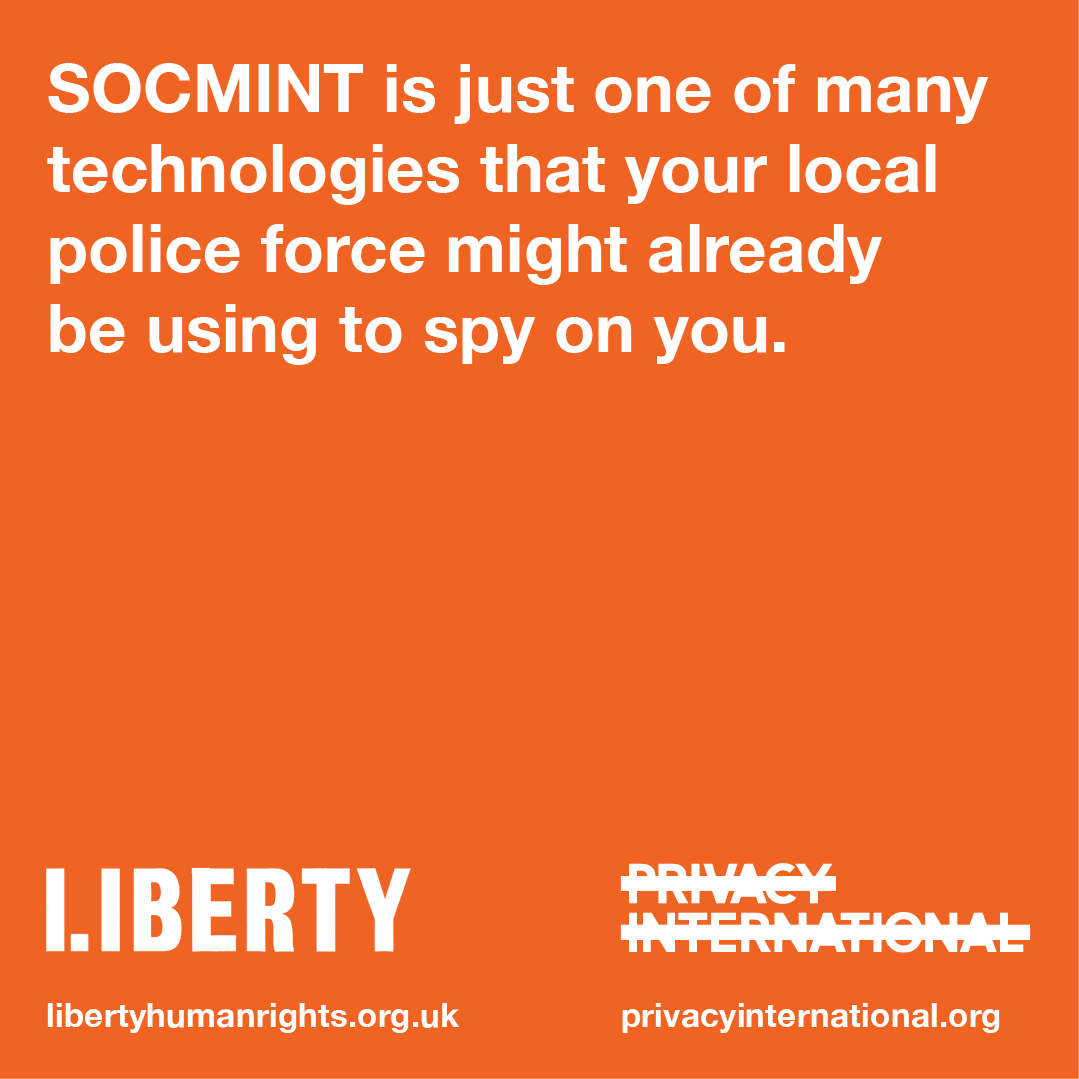
Content type: Explainer graphic
You can also read a more detailed explainer about social media intelligence (SOCMINT) here.
Content type: News & Analysis
At Privacy International, we talk about: “the world being on fire.”We say it to talk about the recurring threats to our democracies, the elections of authoritarian leaders, the current political climate… Or the actual climate. More often than not, we use it to talk about the (lack of) security in the design and implementation of computer systems.
But there is another kind of fire. The fourth wave of feminism – the one that contributed to the protests following the 2012 gang rape of…
Content type: News & Analysis
Image source: Oxfam
This piece was co-authored with Ruhiya Seward, Senior Program Officer at IDRC and originally appeared here.
What if in trying to make development more equitable we’re creating risks that disproportionately impact people based on their gender?
Development programming aims to be both sustainable and equitable in part by recognizing the implications of inequality in its many forms, whether by gender, ethnicity, socioeconomic status, or geolocation. The adoption of the…
Content type: Video
Video courtesy of CPDP (https://www.cpdpconferences.org/)
What is the impact of online gender-based violence on survivors? What should be the role of companies in fighting this phenomenon? What is the link between the right to privacy? In this panel, which took place at CPDP in February 2019, academics, civil society and government representatives discuss the issue of online gender based violence with a privacy lens.
Chair: Gloria González Fuster, VUB -LSTS (BE)
Moderator: Valerie…
Content type: Long Read
For International Women’s Day 2019, Privacy International looks at some of the key themes around the intersection of gender rights and the right to privacy and we review the work we and our partners have done on those topics.
When dealing with cases of non-consensual sharing of intimate images, often known as ‘revenge porn,’ or doxxing, where a person’s personal details are shared publicly, the link between privacy and online-gender-based violence is very clear. Privacy…
Content type: News & Analysis
Creative Commons Photo Credit: Source
In this first episode of the Gender and Privacy Series, we go to Manila in the Philippines to meet two transgender right activists - Naomi Fontanos and AR Arcon. We discuss what the right to privacy means to them and their fight against the government's plan to deploy an ID card system.
Listen to the podcast here.
Content type: News & Analysis
Creative Commons Photo Credit: Source
In the third episode of the Gender and Privacy Series, we talk about sex and privacy with two female activists: Sarah Jamie Lewis, an expert on the security of internet-connected sex toys, and Joana Varon, founder of the female-led Brazilian NGO Coding Rights.
Listen to the podcast here.
Content type: Report
Whose privacy are we fighting for when we say we defend the right to privacy? In this report we take a hard look at the right to privacy and its reality for women, trans and gender diverse people. We highlight how historically privacy has been appropriated by patriarchal rule and systems of oppression to keep women, trans and gender diverse people in the private sphere.
For us, this report is also an opportunity to show how surveillance and data exploitation are also uniquely affecting…
Content type: Virtual Machine
The documentation below is a copy of the documentation found on Github: Interception environment on Github
Privacy International's data interception environment
Version: 2.1.2-20190730
Privacy International's data interception environment
Quick Start Guide
Step 0 - Prerequisites
Step 1 - Download
Step 2 - Importation
Step 3 - Initialising
Step 4 - Setup
Step 5 - Capture
Step 6 - Notes for Android Nougat or Later
Background
Theory
Implementation
Virtualbox (6.0.4)
Debian 10 (Buster)…
Content type: News & Analysis
In December 2018, we revealed how some of the most widely used apps in the Google Play Store automatically send personal data to Facebook the moment they are launched. That happens even if you don't have a Facebook account or are logged out of the Facebook platform (watch our talk at the Chaos Communication Congress (CCC) in Leipzig or read our full legal analysis here).
Today, we have some good news for you: we retested all the apps from our report and it seems as if we…
Content type: Report
6 March 2019
Privacy International (PI) has written Facebook to express our concern and request urgent answers regarding its policy on the sharing of mobile phone numbers of its users.
Alarmingly, recent reports say that some of the phone numbers provided by users for the express purpose of two-factor authentication (2FA) as a way of securing their accounts are now made searchable across the platform by default.
PI is concerned that allowing such numbers to be searchable…
Content type: Long Read
(In order to click the hyperlinks in the explainer below, please download the pdf version at the bottom of the page).
Content type: Explainer graphic
You can also read a more detailed explainer about body worn video cameras here.
Content type: Explainer graphic
You can also read a more detailed explainer about facial recognition cameras here.
Content type: Examples
By 2018, Palantir, founded in 2004 by Peter Thiel to supply tools for finding obscure connections by analysing a wide range of data streams to the Pentagon and the CIA for the War on Terror, was supplying its software to the US Department of Health and Human Services to detect Medicare fraud, to the FBI for criminal probes, and to the Department of Homeland Security to screen air travellers and monitor immigrants. It was also supplying its software to police and sheriff's departments in New…
Content type: Examples
In 2018, the Spanish La Liga app was found to be using the microphone and GPS to clamp down on bars infringing copyright by broadcasting matches without paying. Granting the app the permissions it requests at installation to access the mic and GPS location allows it to turn on the mic at any time. The company says that the audio clips it picks up are converted automatically into binary codes to identify illegal streams but are never listened to.
https://www.joe.co.uk/sport/la-liga-uses-its-…
Content type: Examples
In June 2018, a panel set up to examine the partnerships between Alphabet's DeepMind and the UK's NHS express concern that the revenue-less AI subsidiary would eventually have to prove its value to its parent. Panel chair Julian Huppert said DeepMind should commit to a business model, either non-profit or reasonable profit, and noted the risk that otherwise Alphabet would push the company to use its access to data to drive monopolistic profits. In that case, DeepMind would either have to…
Content type: Examples
In June 2018 Apple updated its app store policies to bar developers from collecting information from users' address books and selling it on. While some apps have a legitimate need to access users' contacts, collecting information unnecessarily is a common money-making tactic. How many apps were affected by the change is unknown.
https://www.washingtonpost.com/news/the-switch/wp/2018/06/13/apple-is-ending-apps-ability-to-secretly-sell-your-contacts-list/
writer: Hayley Tsukayama
publication:…
Content type: Examples
In 2018, an investigation found that children as young as nine in Hong Kong were exposing their identities online via Tik Tok, the most-downloaded iPhone app for creating and sharing short videos. Both Tik Tok and its sibling app Musical.ly, which is popular in Europe, Australia, and the US and allows users to create short lip-synched music videos - are owned by the Chinese company Bytedance. Tik Tok's service agreement says the app is not for use by those under 16. The app has only two options…
Content type: Examples
In 2018, the Brazil-based Coding Rights' feminist online cybersecurity guide Chupadados undertook a study of four popular period-tracking apps to find which best protected user privacy. Most, they found, rely on collecting and analysing data in order to be financially viable. The apps track more than just periods and ovulation; they ask for many intimate details about women's activities and health. The group found that the most trustworthy app was Clue, which is ad-free and optionally password-…
Content type: Advocacy
In October 2018, Privacy International submitted to the public consultation on the “Consolidated Guidance to Intelligence Officers and Service Personnel on the Detention and Interviewing of Detainees Overseas, and on the Passing and Receipt of Intelligence Relating to Detainees” (“Consolidated Guidance”) held by the Investigatory Powers Commissioner’s Office (“IPCO”).
Privacy International’s submission addresses the portions of the Consolidated Guidance on “the Passing and…